Windows Hello Can Be Bypassed Using A Fake USB Camera
Smartphones have been using biometric authentication like fingerprints and faces long before those became more common on laptops and even desktops. Microsoft's Windows Hello framework is its attempt to bring the same mix of convenience and security to its desktop platform, and, for the most part, it seems to work well enough. New security research, however, reveals a fatal flaw in Windows Hello's face recognition process that could bypass authentication using a custom-made USB device. Fortunately, exploiting that in real life isn't as simple as the flaw itself.
The process that security researchers at CyberArk went through belies how easy it is to fool Windows Hello, or at least its facial recognition system. Windows requires that a PC has a camera with both RGB and IR sensors for Windows Hello face recognition to work. It turns out, however, that it is really only data from the IR sensor that's critical to bypassing Windows' security.
The researchers developed a USB device from an NXP evaluation board that presented itself as a USB camera with RGB and IR sensors. In reality, however, the device just sent premade image frames: some IR frames of the real owner and some RGB frames of Spongebob. After several tests, the researchers discovered that they really needed only one IR frame and a plain black RGB frame to fool Windows Hello.
According to CyberArk, the vulnerability exists because Windows Hello allows external devices to act as data sources for biometric authentication. On the one hand, it has no choice but to do so since not all Windows PCs have built-in cameras or fingerprint sensors. On the other hand, the research proves that it is also the weakest link in what should be a foolproof security system.
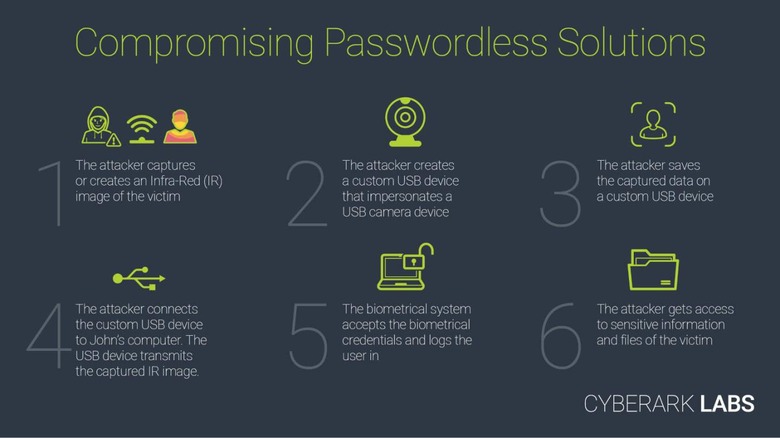
Fortunately, it's not exactly a horror story waiting to happen. In order for an attacker to exploit this weakness, they need to get IR images of the target's face, and that's no easy feat. They would also need physical access to the desktop or laptop, and, at that point, there could be other ways to get into the system anyway.
