Remote Webcam Activation Without Warning Light Confirmed: Johns Hopkins
Researchers at Johns Hopkins University have positively confirmed the long-discussed ability of government entities and private parties to remotely activate a webcam without the warning light turning on. While this privacy vulnerability has already been anecdotally admitted by a variety of sources, this research is the first time it has been proven by an established public-facing organization. The results were published last week in a paper entitled "iSeeYou: Disabling the MacBook Webcam Indicator LED".
The paper focused on Apple iMacs as well as MacBooks. Specifically, it focused on pre-2008 models of the iMac G5, as well as "early Intel-based iMacs, MacBooks, and MacBook Pros," according to the Washington Post. Those models' built-in iSight webcams were the targets of the researchers' academic hacking efforts. They were able to remotely turn on target iMac and MacBook computers' iSight webcams without activating the LED that lets users know they're being observed.
Yet the researchers insist that the results apply to the webcams on current MacBooks, iMacs, and all other types of PCs. The only reason they focused on older Apple models was because their less-secure equipment was less cost-prohibitive to hack. If they had had a larger budget, they appear certain they could duplicate the results with the latest models. It's just a matter of how many layers of security they have to uncover.
The vulnerability rests in the microcontroller found within the iSight camera itself. The microcontroller is the computer that controls the camera activation as well as the LED warning light activation. It is separate from the rest of the computer and thus not as subject to the security protocols built into the (separate) CPU. Hacking directly into the webcam's microcontroller allowed the researchers to duplicate the security breaches that have popped up in recent years, as in the famous case of Teen Miss USA Cassidy Wolf, whose webcam was hacked by a 19-year-old former high school classmate.
The image below depicts the iSight components the Johns Hopkins researchers were able to infiltrate.
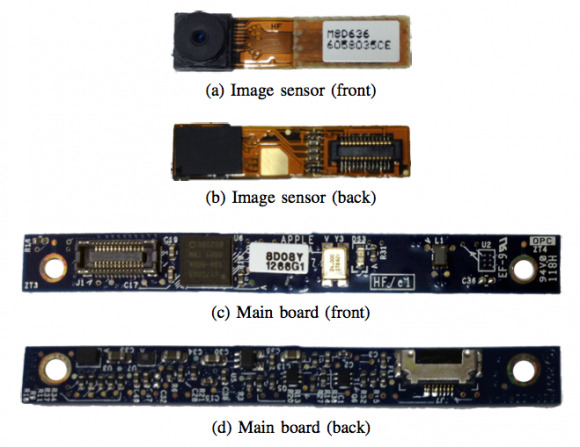
Webcam hacking has been used for years by law enforcement. Former FBI Operational Technology Division in Quantico assistant director Marcus Thomas revealed a couple of weeks ago that the FBI has been covertly activating webcams "for several years." Technically the agency is only allowed to do it with a court order, and the tactic has only been used in-agency a few dozen times and only in "extreme" cases.
Yet the vulnerability is out there, and it has now been confirmed by an institution of higher education. The Post even demonstrated in a video how it can be done by using the research team's home-brewed webcam hacking software it used to carry out the tests on the iMacs and MacBooks.
In the meantime, you can protect yourself by applying a bit of low-fi security: a piece of tape or a Post-It note. Or, if you want to avoid gumming up your device or putting scratches in it, you can go the commercial route with something like the Peep Shield or Eyebloc.
There's just one problem remaining: audio. The FBI and the Johns Hopkins researchers both say secret remote microphone activation is just as handily accomplished. We're not aware of any widely available security measure against unannounced microphone hacks as yet. If you know of anything, let us all know in the comments.
SOURCE: Washington Post
