Tech Privacy 101 - Ways To Keep Private Things Private
Privacy is no longer a concern of a few well-informed, conscious, or even paranoid individuals. Given how much of our lives we have stored on computers, phones, or the cloud, digital privacy should already gain the same level of attention that we give our physical spaces. Sadly, that just isn't the case and many, sometimes even the best of us, take such things for granted. And with governments seemingly more invested in actually invading citizens' privacy, the responsibility of securing our digital lives falls on us. Fortunately, you don't need to be a computer scientist nor a lawyer to implement these simple steps to protect your privacy, whether online or offline.Know your settings
This should be your first line of defense. Many platform and software makers are required, either legally or by popular convention, to give users the choice to opt out of features and settings that would submit their data to HQ. Sometimes, however, those settings might be buried under tons of other settings or are worded so poorly to be of any use. That said, the Web is littered with instructions on exactly what they mean and how they will affect you.
It pays to know what those are and turn them off from the get go. From Android to iOS to Windows 10, operating systems are riddled with switches to submit your data to the platform makers, some less innocent than others. Even those "telemetry" settings that send data back to Google, Apple, or Microsoft to improve or fix the software often have some data attached. Of course, they promise not to use those for evil, but you, not them, should be the one to decide when or even if you want to send such data to them.
Hide your location
Related to the above are the location tracking settings that are often the most used and most abused that it deserves its own treatment. Some apps do use such data to actually be useful, like mapping or ride hailing apps, but some have no business knowing where you are or where you've been. And even those that do shouldn't be peeking 24/7.
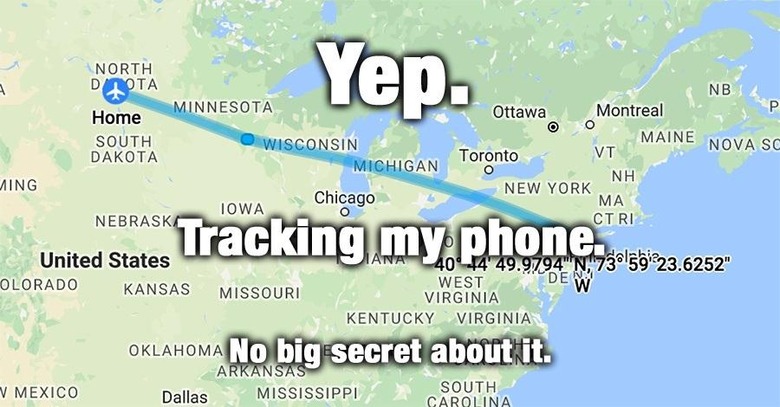
Fortunately, it's not impossible, not even difficult, to disappear from the map. Virtually, of course. Just follow the handy guide our own Chris Burns just wrote to make sure you're steps aren't being tracked without your knowledge, much less your permission.
Use strong passwords, or a password manager
Passwords are the primary gateway to much of our online identities, even with such measures as two-factor authentication. Just like in the real world, it makes sense to protect your property with locks. And not just any lock but a sturdy one.
Sadly, that line of thinking seems to fly out the window when it comes to passwords. To the point that there is a thriving industry revolving around creating strong passwords for you and keeping them safe so that you won't have to. Take advantage of those but also be aware that you are, in effect, putting your eggs in their basket.
Use a passcode/PIN/fingerprint
Passwords are great for online accounts, but you should also put a lock on you devices. Most people seem to be too obsessed with immediately unlocking their phone that they're willing to settle for a simple swipe to unlock. Fortunately, technology is catching up with our habits, providing fingerprint and iris scanners to keep our devices secure without using too much of our precious seconds to enter a PIN or passcode.
But if your phone doesn't have that feature, a 4-digit PIN, which locks the phone completely when failing at least thrice, is still better than nothing. As long as it's not "1234".

Encrypt your phone
In the worst case scenario that your phone falls into the wrong hands, your last line of defense will be encryption. Both Android and iOS now offer the ability to encrypt your phone for added protection and, most of the time, with very little performance impact. This is sometimes best done one a new phone but not impossible to do on an existing device. Just be sure to backup your data, in case things go awry.
PCs, especially long-running ones, are a harder case, but, again, not impossible. Encrypting them, however, might require a bit more expertise, or at least assistance from someone more knowledgeable.
Beware of links
Most of the malware, hacks, and intrusions of privacy start one way: when a user unwittingly clicks on a link, opens an e-mail, or runs an untrusted program. Be suspicious of links you receive in e-mails, even if they come from trusted people (who, themselves, may have been compromised). And always double check the spelling of such links. A single typo can mean the difference between a clean system and a hacked identity.
Open Wi-Fi isn't always safe
Closely related to this is open Wi-Fi hotspots. Free might be tempting, but unless you're sure you're connecting to the right one, better not. Malicious individuals often masquerade such hotspots, luring unsuspecting users into their web. A man in the middle attack, one of the most popular types of intrusions, is easiest to pull off when attacker and victim are on the same network.
And in the case you have no choice, the next two can help keep you safe even in open Wi-Fi networks.
Use a VPN
Virtual Private Networks may have an image of being used by pirates to circumvent geographical restrictions, but the technology in itself is used for more than that. In fact, enterprise software that lets you access company computers remotely, like those that BlackBerry offers, employ VPN or a form of it.
VPNs are immediately useful in covering your tracks when you're on the Web or masking where you're coming from. It is also useful, as implied above, in protecting yourself in open Wi-Fi networks. VPN services have fortunately become easier to use and setup and it no longer requires a genius to take advantage of one.
Browse Incognito
If you can't use a VPN, at least try to browse in incognito or private mode. While it won't make it seem like you're browsing half a world away, it at least makes sure that websites, ads, and even the browser itself, aren't tracking your movement. It's no panacea but it is the easiest way to ensure your privacy online. Some apps, like Mozilla's Firefox Focus, actually only browse in such a mode.
Only download from trusted sources
Apps can be fun, but not all of them can be trusted. Especially if you get them from unofficial sources. Third-party app repositories, especially those promising free versions of paid apps, often carry some malware or another. Of course, not all of them do, but one should always proceed with caution.
That's harder to do on PCs and Macs, where it's too easy to download installers left and right. As a rule of thumb, only download straight from the horse's mouth. Even official mirrors should be held suspect.
Wrap-up: Know what you are signing away
Every software or service today has a privacy policy, many of which are made intentionally obscure. It is perhaps best to presume that they all take some of your data and send it home. How much they do is really the only thing that varies. You can reject those privacy policies, but, of course, that usually means you won't be able to use their software or service.
And you don't really have to give those up. The choice is really yours. But at the end of the day, you should be aware of what you're giving up, what you're sacrificing, and what you're putting at risk by clicking "I Agree". If you're willing to live with those, then go wild. Just don't be shocked if you see your email in Yahoo's/Altaba's next big bombshell.
