Synology: Update Your NAS Because We Can't Rescue Ransomware Files
NAS-maker Synology has spoken up on the recent "ransomware" attack on its network drives, advising owners to upgrade to avoid the risk of their files being nefariously encrypted and then be extorted afterwards. The exploit used by SynoLocker was patched back in December 2013, Synology says today, but relied on owners actually updating the firmware of their drives to apply the fix. That means it's bad news if you've already been hit by the ransomware.
According to Synology, the susceptible versions of DSM – its DiskStation Manager OS – are DSM 4.3-3810 or earlier; DSM 4.2-3236 or earlier; DSM 4.1-2851 or earlier; and DSM 4.0-2257 or earlier. The primary advice is to update to DSM 5.0, which has included patches for the vulnerability since late last year.
By default, though, Synology NAS aren't set to automatically update as each DSM version is released; that's an optional setting for users to actively choose. As a result it's possible that owners could be relying on a shared drive that is several versions behind.
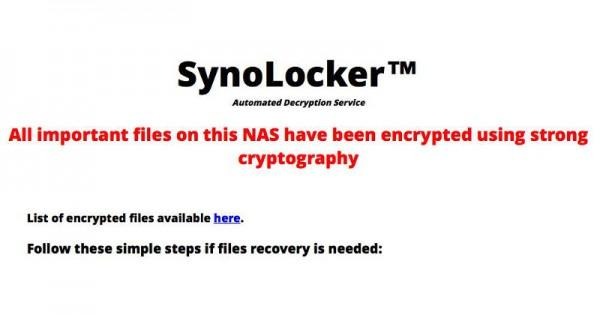
The risks that open up, at least in the case of SynoLocker, are considerable. Some users have tried to access their files, only to be told that the data has been encrypted and that they'll need to cough up a fee to regain access. According to victims, the going rate is 0.6 bitcoin, or roughly $349 at today's rates.
Synology can help recover the drive's core functionality, the company says, but it "is unable to decrypt files that have already been encrypted," it warns.
If your Synology NAS is showing "abnormally high" CPU usage, or you spot "synosync" among the running processes then it might be time to worry. Synology recommends unplugging it immediately and getting in touch with the support team, in the hope that not all of the files on the drive are affected.
