SMS Two-Factor Authentication Is Unsafe - Use These Instead
The revelation of Google's Titan security key has put the spotlight on a long-existing but not widely adopted technology: physical keys that open the doors to your digital life. FIDO-compatible security keys, strange as they may seem, is just the latest attempt to solve one of the biggest threats to digital security: passwords. But while two-factor authentication is finally gaining a bit of traction, thanks to services enforcing it, they are unfortunately using the least secure medium of all: text messages.
”123456” and “password”
It seems that humans are naturally terrible at keeping secrets and remembering where they left their keys. A weakness in the physical world, those traits have bled into our digital lives as well. On the one hand, who can you blame when the strongest passwords have to be an indecipherable string of letters and numbers that is nearly impossible to memorize. Multiply that by the number of accounts you have and you can see where password managers get their business.
Rather than forcing humans to learn better password habits, which has been unsuccessful for decades, we have instead learned to employ technology to apply a band-aid to the problem. That's how two-factor authentication or 2FA was born and it used the communication channel that was immediately available to all, which also happened to be the most insecure.
Lowest common denominator
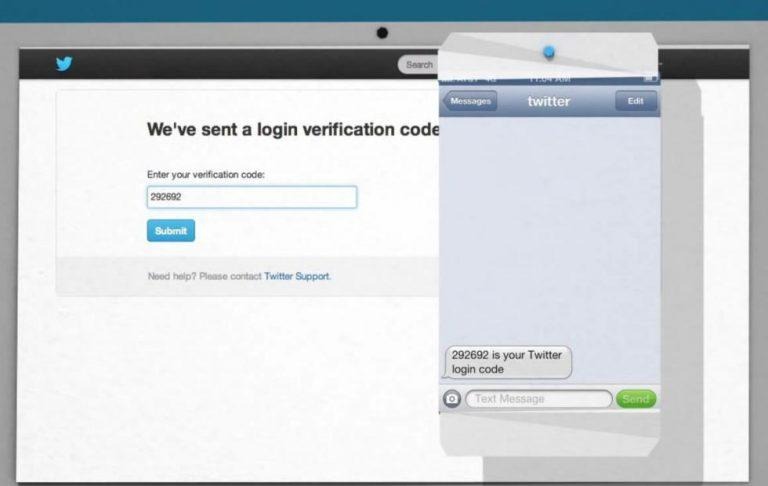
Most two-factor authentication these days send a one-time PIN (OTP) through SMS to verify a login attempt. Depending on network quality, it's fast, easy, and everyone with a phone can use it. It doesn't even have to be a smartphone, just a regular phone with text messaging capabilities is enough. It's no puzzle really why it's the most common 2FA method.
SMS, however, was born at a time when things like encryption was not really widespread even if they already existed. SMS was built to be fast and light for fledgling networks to implement and support. Unfortunately, it never outgrew those limitations and, to this day, it is still the most vulnerable protocol in wide use.
But forget about man in the middle attacks and snooping. A convincing hacker can, in fact, dupe carriers into giving them access to your phone number or SIM. It's only recently that carriers have wised up on the strategy and started to be more cautious. But by then it was already too late. SMS 2FA has become the norm and it's like having a key but putting that key in a very visible place within anyone's reach.
Authentication apps
That is also the reason why the tech industry is trying to push for a different 2FA method: apps. Google is, unsurprisingly, at the forefront of that thrust but if you don't trust it enough, there are still plenty of authenticator apps to choose from, like Microsoft Authenticator (OK, maybe not a better option), Authy, LastPass, and 1Password, just to name a few. These apps aren't tied to a particular phone number and don't use the insecure SMS channel.
There is some level of inconvenience here, of course. The biggest one is that it does require you to have a smartphone, particularly Android or iOS. Any smartphone will do, of course, and almost everyone has one these days. They are also superficially bound to a device. If you lose that device or uninstall the app, you can potentially lose access to accounts that use this 2FA method. Of course, they often give you "recovery codes" or have a fallback options (usually email or even SMS). It's harder than SMS, naturally, but is as it should be.
Security keys
That is also partly the reason for this relatively new trend of having security keys. It's almost ironic that we are back to using physical keys even for completely digital locks. Security keys mostly do away with the need for authenticator apps and require either just the key itself or, for added protection, your fingerprint.
Of course, given humans' propensity to lose keys, it is almost tempting fate. Fortunately, it is easy enough to program a new key while invalidating the old one. Enterprise customers also love it because it gives them more control over who can access what, and admins just love to be in control.

Beware of Social hacking
These three 2FA methods, SMS, apps, and hardware key, demonstrate increasing sophistication in keeping our digital lives secure. They are, however, all band-aids to the real problem. Better band-aids but still just temporary fixes. They can protect accounts and files from technological attacks but they have proven to be inadequate to the most serious attack of all: social hacking.
Call it social engineering, phishing, or just plain conning, social hacking attacks the weakest link in the security chain. You are, of course, less likely to simply hand over a physical key to a complete stranger, but good social hackers need only to observe a target to find their weaknesses and habits. We are, after all, creatures of habit and, unfortunately, we have collectively developed the worst security habits imaginable.