Simplelocker.A Ransomware Targets Android SD Card Data
There is another ransomware lurking around the Android neighborhood and this time it can actually do more harm. This Simplelocker.A malware targets a device's SD card and encrypts common file formats in there so that users can't access them unless they pay the price.
Android's security has always been a topic for debate because of how open the system is, at least compared to other mobile platforms like iOS that are described as "walled gardens". Google's platform certainly has had its fair share of malware and security exploits. Just last month, a certain type of ransomware named Koler.A was reported. This malware locked users out by always displaying a window on top of the screen, but otherwise did not harm the user's data.
In that sense, this Simplelocker.A reported by security suite maker ESET is more malicious and definitely more dangerous. Once the malware is installed, it scans the device's SD card, if it has one, and encrypts popular file formats using the AES encryption algorithm. These include Word document files, MP4 videos, JPG and GIF images, and more. The malware will then display a message, in Russian, informing that user that he or she has been locked out because of viewing illegal pornographic material. Of course, it also gives instructions on how to deposit what amounts to $21 through an untraceable electronic money service in order to get those apps decrypted.
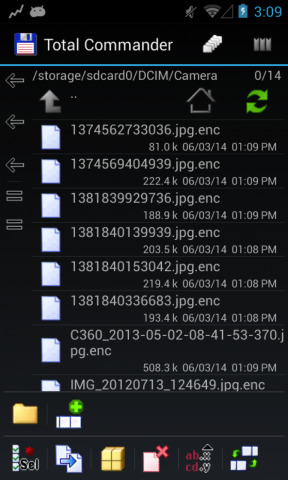
According to ESET, however, that may not exactly work out that way. Their code analysis reveals that the malware communicates with a server, hidden behind a TOR network, and sends essential user info, including the IMEI. The malware itself does not have code to decrypt the files on its own. ESET's theory is that the command to decrypt is sent by the remote server only when payment has been received. This practically means that the malware source could simply decide not to do his or her part even after the ransom has been paid.
Simplelocker.A isn't exactly something most user's will encounter. For one, the current malware rides on a porn app that isn't found in Google Play Store. The only way it can be installed, then, is if the user consciously bypasses Android's usual security checks, in which case the blame partly falls on the user. This also makes a case for Google's unfavorable opinion of external storage, where it can't enforce strict security and integrity checks the way it can on internal memory. Recent source code changes in the Android Open Source Project repository suggest that Google might be moving towards restricting access to SD cards, much to the worry of developers and users who expect unfettered access to their data storage.
SOURCE: ESET