Java Tipped In Red October - May Be Homeland Security's Hang-Up
Over the past several days, the US Department of Homeland Security has issued warnings against using Java due to newly discovered security weaknesses – today it's been tipped that the Red October cyberespionage attacks may have had their own Java iterations. The two have not been put together by the Israeli IT security firm Seculert, the group that today suggests Red October was implemented not just via email downloads and USB sticks, but through web-based Java exploits as well. Could that and Homeland Security's warning be timed both right here at this point in time together without any relation to one another?
Coincidences like this don't just happen every day. According to Kaspersky Lab, the antivirus group that let loose the info on Red October earlier this week, it was mainly through Word and Excel documents that the security exploit was delivered, either via an email download or possibly through USB sticks plugged into host computers. Security researchers from Seculert assigned to analyze the command and control servers used in the Red October campaign have found a malicious Java applet made to exploit a Java vulnerability they say was patched all the way back in October of 2011.

What this means is that their targets were not computers that were brand new, patched and up to date, but older machines that for one reason or another hadn't gotten with the program. Another fabulous reason to keep your computer up to date, that's what this is. According to the Seculert blog where the Java connection announcement was made, "the JAR file of the Java exploit was compiled in February 2012, even though the patch for the vulnerability was available as of October 2011."
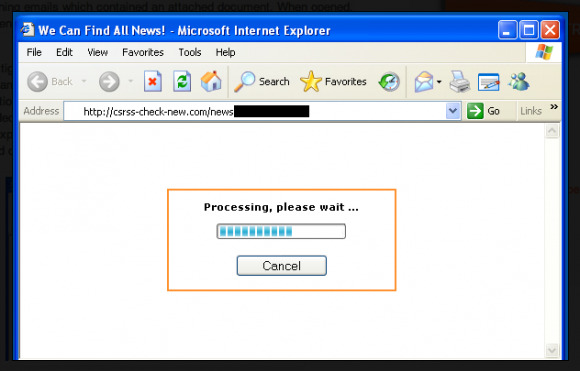
These exploits appear to have been included in pages with the title "We Can Find All News!" The terms "news theme" and "NewsForYou" were also included in the code, this leading the team to believe that it was through a series of pages that suggested they'd be delivering the malicious project via harmless-seeming websites with "fake" news blasts galore. While it would seem strange that the US Department of Homeland Security would wait many, many months to deliver a warning against an attack like this, it is possible that, like the rest of us, they only found out about it here in 2013 – and they've not confirmed that this is the same attack, of course, but we shall see!