iPhone Exploit Active "At Least Two Years" Detailed By Google
An iPhone exploit that impacted several generations of iOS up to iOS 12, and which could potentially see malware installed on a device simply by visiting a hacked site, was quietly patched by Apple earlier this year, Google's Project Zero has confirmed. Fourteen vulnerabilities were spotted by the search company's security researchers, which if used maliciously could have been used for so-called watering hole attacks.
Such attacks bypass targeted hacks on specific devices, or even encouraging users to inadvertently install malware or other compromised software through spam and other means. Instead, attackers simply set up websites which take advantage of vulnerabilities in a device's software.
Known as exploit chains, such sites use a rare sequence of vulnerabilities to bypass a device's security. Assuming they're successful, they can take a device to the point where malware can be secretly loaded to it.

Five separate, and unique, iPhone exploit chains were identified. Collectively, they spanned versions of iOS 10 through to iOS 12. It wasn't just a theoretical exploit, either: according to Project Zero, they identified "a group making a sustained effort to hack the users of iPhones in certain communities over a period of at least two years."
It's unclear at this point what data that group was trying to – or indeed able – to obtain from devices, which communities were targeted, or how many iPhones they may have compromised in the process. Still, in testing, the scope of the potential damage is significant. The implant used was technically able to obtain iMessages data, photos, and real-time GPS information about the location of the iPhone.
"There was no target discrimination," Ian Beer, of Project Zero, explains, "simply visiting the hacked site was enough for the exploit server to attack your device, and if it was successful, install a monitoring implant. We estimate that these sites receive thousands of visitors per week."
Google's security team notified Apple on February 1st, Beer writes, with a 7-day deadline. Apple subsequently released iOS 12.1.4 on February 7, 2019. A security bulletin accompanying the update described several fixes to Foundation and IOKit.
Apple has not commented further on the vulnerabilities.
It's not just the Cupertino firm's own software that is of concern, mind. Further testing by Project Zero showed how malware installed through the exploit could have access to databases for popular messaging apps like WhatsApp, Telegram, and Google Hangouts. Some of these are popular for their promise of end-to-end encryption, the assurance that nobody other than the intended recipient will be able to read the messages sent.
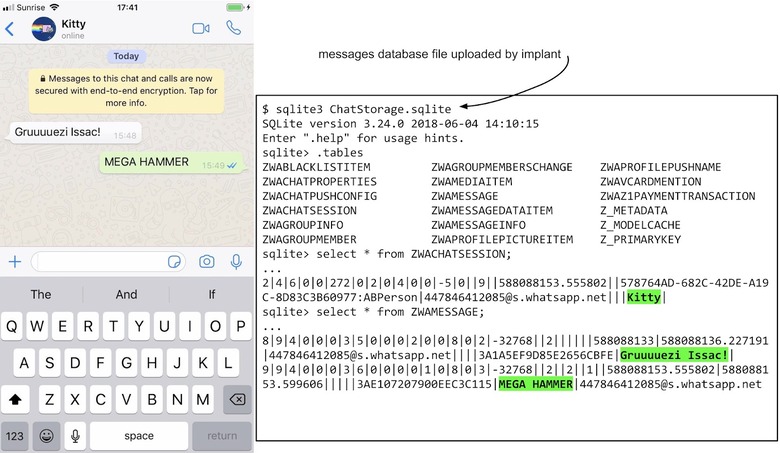
With database file access, however, unencrypted, plain-text versions of messages could be extracted from those apps. The hack was demonstrated on an iPhone 8, running iOS 12, with the malware attempting to steal files every 60 seconds.
Still, there are some caveats worth bearing in mind. For a start, Project Zero highlights, the implant binary isn't persistent after a reboot. Restart the iPhone, and it will take another visit to a compromised site to add the malware back in.
