Heartbleed Bug: Vulnerable And Patched Sites Chime In
When you think about the scope of the Heartbleed bug, you have to consider that it was (and is) allowing hackers to see data – any data – stored on servers. This data vulnerable to CVE-2014-0160 (aka Heartbleed) is not limited to certain kinds of data – it's anything and everything. So what's to be done?
We've already written a SlashGear 101 article by the name of Heartbleed bug: how to avoid this massive web hack. We've also got an article about the first web extension and detector for Heartbleed, allowing you to see if your site – or a site you're using – is vulnerable.
Now it's time we have a look at some major sites that are still vulnerable and some sites that've stepped up and patched. SlashGear is a site that's been patched for a while – we saw this bug before it became a problem and our master robot fixed it. Even before it was apparent that this blip was more than a blip, it was fixed – we don't like blips, no matter how tiny.
One site that's doing the fix process right is Wunderlist. According to @DoubleJake, an email was sent out today suggesting users reset their password and that they've had their OpenSSL software updated.
TIP: Unless you're sure a vulnerable site has been patched, DO NOT reset your password at this time. Resetting your password before Heartbleed is patched out would be like having a lit match in a puddle of gasoline, realizing your danger, putting the match out, and lighting another match without stepping out of the gas.
According to Errata Security (ErrataSec), their "masscan" test turned up 28,581,134 sites on the web with valid SSL connections. This scan shows 615,268 of these sites to be "vulnerable to the Heartbleed bug."
In addition to this 615,268 sites vulnerable to Heartbleed, 330,531 sites had heartbeats enabled but "did not respond to the Heartbleed attack." It's reasonable to assume that these sites have been patched with the newest version of OpenSSL, and are now no longer vulnerable to the attack.
It's also important to note that because some IP addresses redirect port 443 traffic – that's where this test comes in – to a single load balancer, these counts aren't perfect. This is only an OK indicator that the web has already started to be patched.

Over at Tumblr you'll see that Yahoo's blogging engine has been patched. Oddly, it seems that their advice is to "call in sick and take some time to change your passwords everywhere".
We must reiterate at this point that this is not the immediate and final answer for everyone right now. Check your favorite sites for vulnerabilities first, make certain they're patched, then change your passwords.
Google has also made clear that they are patched for Heartbleed in many sectors. Search, YouTube, Wallet, Gmail, Google Play, Apps, and App Engine are all patched, while Google Chrome and Chrome OS were never affected in the first place.
Users of Google Cloud Platform or Google Search Appliance are being warned in a variety of ways to get their butts in gear for a fix. Cloud SQL is being patched today and tomorrow. Google Search Appliance is working on a patch and will post an update within 24 hours of April 9th at 9:58AM PST at Google Enterprise Support.
Google Compute Engine users need to do some work – as fast as possible. Users working with Google Compute Engine need to manually update OpenSSL on ever running instance – Google also recommends that if this is not possible, users should replace every existing image with versions with the patched, updated version of OpenSSL.
All updated instances working with Google Compute Engine should be rebooted once the update is initiated. Google Compute Engine goes through this process in fine detail.
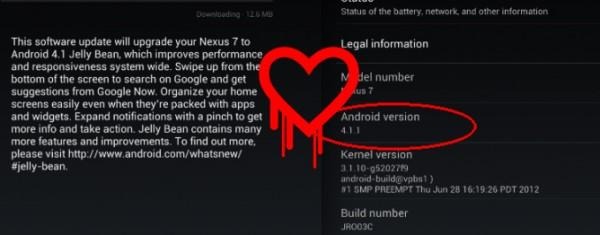
Google's final warning is for Android – but fear not. Only one single version of Android is out there with the Heartbleed vulnerability, that being Android 4.1.1 Jelly Bean. All other versions of Android are immune to Heartbleed.
If you're especially jumpy about Heartbleed and your smartphone is running Android 4.1.1 today, you might just want to set it down and walk away, waiting then for your carrier to send out an update.
