Gmail PSA: This Phishing Scam Is All Too Easy To Fall For
A simple but astonishingly effective Gmail scam continues to compromise even adept internet users, with phishers taking advantage of how browsers present URLs to steal emails and other information. The exploit presents users with what looks like a regular login page but, rather than being hosted by Google, is in fact running on a different server waiting to steal account details. What sets it apart in phishing terms is how well that server is hidden.
Usually, by looking at the browser's address bar, you can see whether or not a page is being hosted on the correct Google server or not. Email scams which rely on people punching in their credentials to pages masquerading as official Google sites are commonplace, but typically a cursory glance reveals that they're actually on a different server altogether. This latest exploit, though, hides that face.
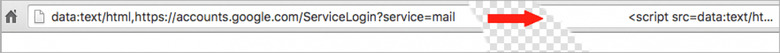
By using what's called a "data URI", a long string of text is put into the address bar. That both mimics the "accounts.google.com" address that users often know to look for, and pushes the rogue URL that's actually being visited out of sight. If you click it, and then enter your account details, going by previous victims the hackers quickly access your email and send out compromised messages to your contacts, propagating the exploit.
At the same time, they have full access to the contents of your inbox and sent messages, and could potentially leverage that to reset passwords on other sites like online banking. That's potentially without the user even knowing, though they could alternatively change the password and lock the legitimate owner of the account out completely.
In a statement from Google provided to Wordfence, spokesperson Aaron Stein said that the company is looking into how it could better protect users from such exploits. Stein would not be drawn on what, exactly, that might include, though tells Wordfence that there should be some movement on that front "soon". One possibility is another indicator in the address bar that would flag misleading URLs of this sort.
"We're aware of this issue and continue to strengthen our defenses against it. We help protect users from phishing attacks in a variety of ways, including: machine learning based detection of phishing messages, Safe Browsing warnings that notify users of dangerous links in emails and browsers, preventing suspicious account sign-ins, and more. Users can also activate two-step verification for additional account protection." Aaron Stein, Google
As for how to avoid getting hacked yourself, the advice is pretty straightforward. For a start, if you haven't already done so you should enable two-factor authentication, or "2-step verification" in Google terms. That adds a second layer of security to your regular password, requiring a special one-time code that's generated – or sent to – your smartphone.
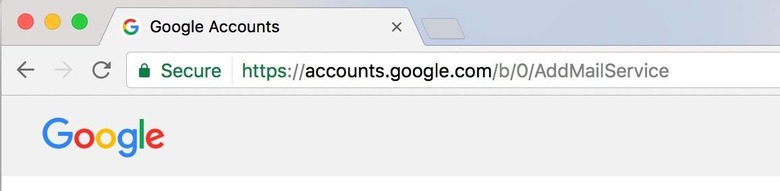
Beyond that, it's vital to check the address bar in your browser whenever you're faced with a page asking for your Gmail credentials. The URL should be preceded with "https://" and, if you're using Chrome, it – and the lock symbol – should be green. The URL "https://accounts.google.com/" should be uninterrupted.
If you believe you've clicked on a compromised link, meanwhile, it's good practice to change the password not only on your Gmail account, but any other account which uses the same credentials. In the case of an email exploit like this, that means not only any site which uses your email/password set as a login, but any other site which may have sent you an email as that could give hackers a head-start on what to try breaking into next.
MORE Wordfence
