Chrome, Firefox Has Been Leaking Facebook Profiles, Names Since 2016
Facebook just can't seem to catch a break and has become everyone's favorite scapegoat for privacy problems. Sometimes, however, it's not exactly Facebook's fault. Case in point is a recently reported and, fortunately, fixed vulnerability that allowed malicious third-party sites to glean Facebook information like a user's profile picture and name. And that vulnerability, ironically comes from a standard Web feature that was introduced way back in 2016.
This is what is called a side-channel attack since it is caused not by a flaw in the software itself but in the system it is running on. In this case, the vulnerability is due to a new feature introduced in the CSS (Cascading Style Sheet) standard in 2016. Called "mix-blend-mode", it practically leaked visual content, technically the pixels, on a Facebook page to a third-party website that embeds Facebook inside an iframe.
Normally, that shouldn't be the case because of a same-origin policy implemented by web browsers. Of course, if that were the case, then this vulnerability wouldn't exist in the first place. The bug doesn't directly extract images or text from Facebook profiles though. Instead, it analyzes each pixel and, in the case of text, uses optical character recognition to extract meaningful words like names or even posts. It might seem like a lot of work, but it only takes a computer 20 seconds to do all that.
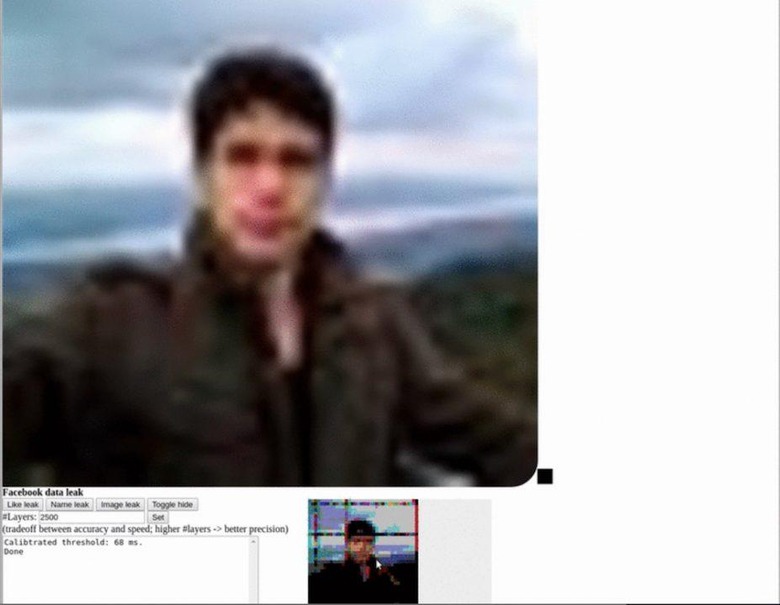
According to Ars Technica, security researchers Dario Weißer and Ruslan Habalov disclosed the vulnerability to Google and Firefox, who have patched their browsers by now to block future attempts. That, however, still left many people unprotected between 2016 and late 2017 at the earliest. The researchers report that, for reasons still unknown, Apple's Safari browser was unaffected. Almost ironically, Microsoft's Internet Explorer and Edge browser were also unaffected because they didn't even implement the standard mix-blend-mode feature.
Sadly, that's not the end yet. While this particular side-channel vulnerability has now been closed, Weißer and Habalov worry that it might just be the start. As Web technologies and standards become more sophisticated and utilize hardware more, the chances for such vulnerabilities to pop up becomes even greater.
