Beware The Meitu Photo Filter App - It Just Stole Your Phone's ID [UPDATE]
It's time to uninstall Meitu, the photo app masses of users downloaded over the past week to make their selfies look wacky. This app was found today to be sending IMEI numbers to several China-based digital locations. That alone isn't enough to do a whole lot, but given the massive amount of permissions the app seeks (and is granted) when it's installed, the app has effectively given someone in China the ability to take control of the phone it's installed on. In other words – uninstall Meitu (and any apps made by the same company) IMMEDIATELY and consider changing all passwords of apps and accounts associated with your smartphone.
While the app MEITU has been out on the app market – on more than one app market – for several years, it's only very recently become mega-popular. In just the past day, thousands of users have installed the app (and similar apps from the company) for the first time. While it IS POSSIBLE that the people behind this app do not mean to be doing anything malicious with this data collection, the potential for unsavory actions as a result of this information transfer are too high for us to ignore.
Of special note: The title of this article uses the word "stole" because the app itself does not make mention of use or transfer of your smartphone's IMEI number. It also does not mention specifically the sending of most or all of the data points listed below. Without your permission, this information is being transferred from your phone to a series of unidentified locations in China.
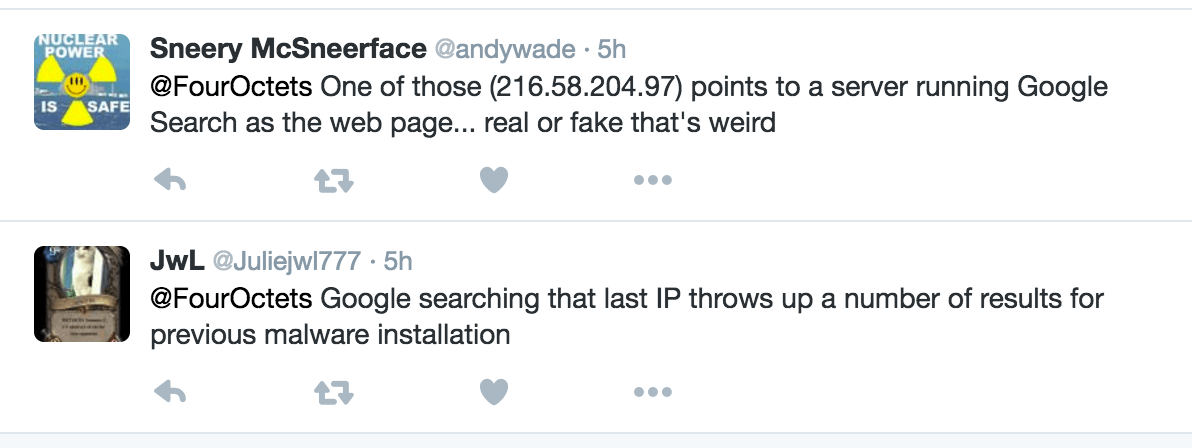
As FourOctets mentions, destinations include the following – and a litany of others. These addresses land in various locations inside China.
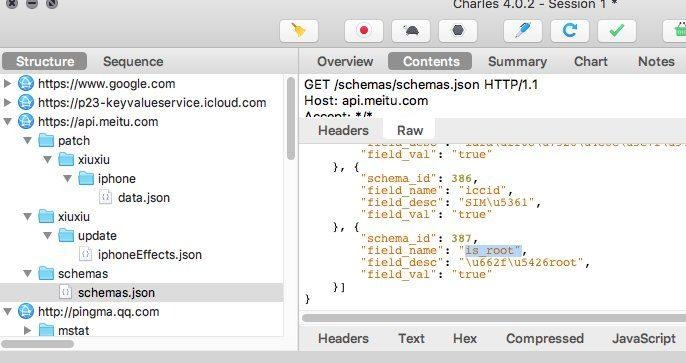
Further investigation from Jay Bennett on Twitter (and seconded by Infosec user / reverse engineer Greg Linares) shows additional info being stolen by the app. Information includes a bit about root, SDK version, carrier, OS type, Mac Address, etcetera. Basically it would seem that the folks behind the info sent by Meitu are looking for devices that have root permission, that opening up the door for them to take control of phones in a big way. With root (and other information on this list), these users would be able to take control of the device's functions – including cameras, if they did so wish.
Bennett's found list of information sent to a China-based server (and malicious users, more than likely), includes the following:
• App Key
• App Version
• OS Type
• IMEI
• Mac Address
• OS Version
• Device Model
• Resolution
• Carrier
• Network Type
• Language
• Country
• City
• Longitude
• Latitude
• SIM ICCID
• Local IP Address
• Root Status
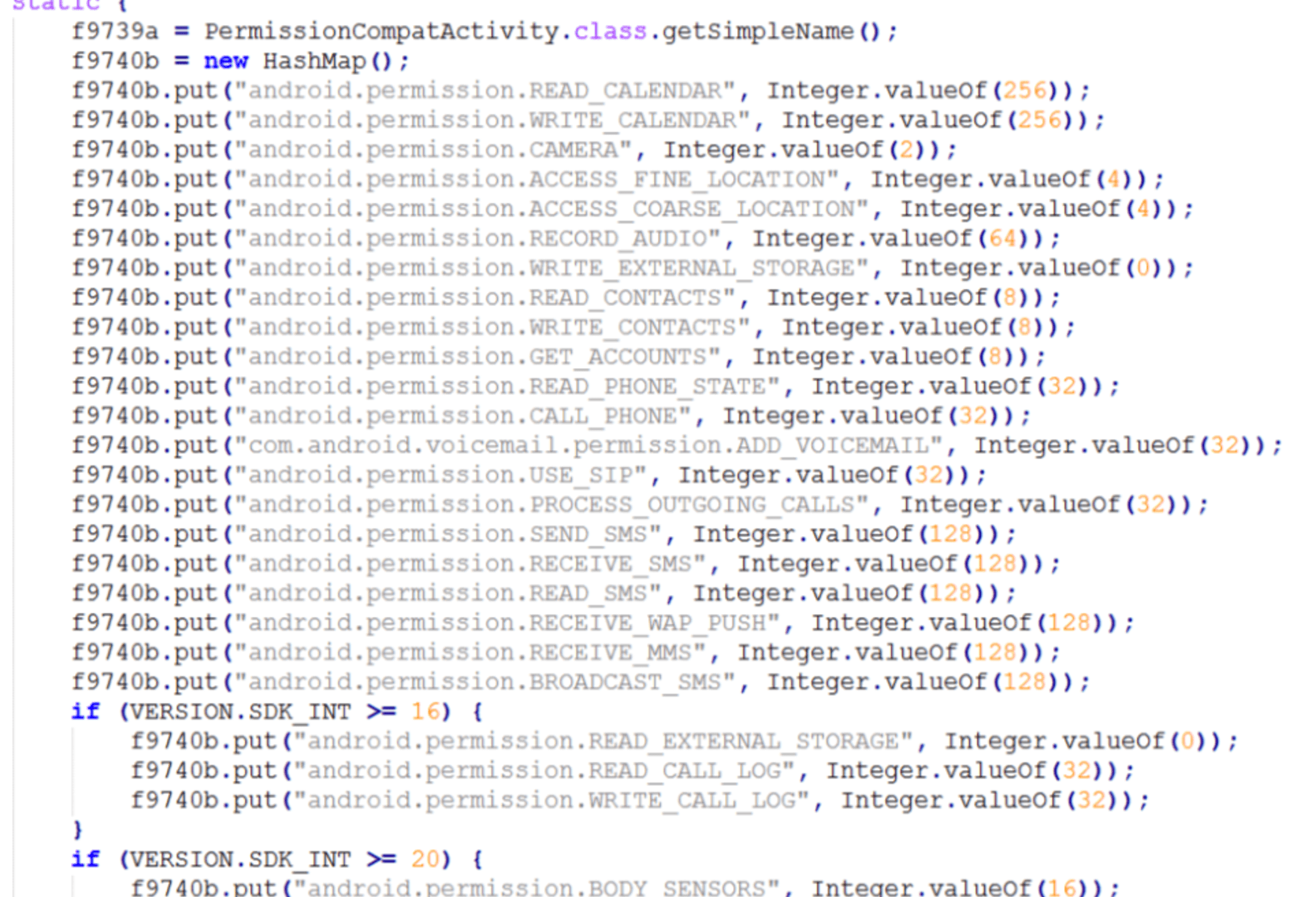
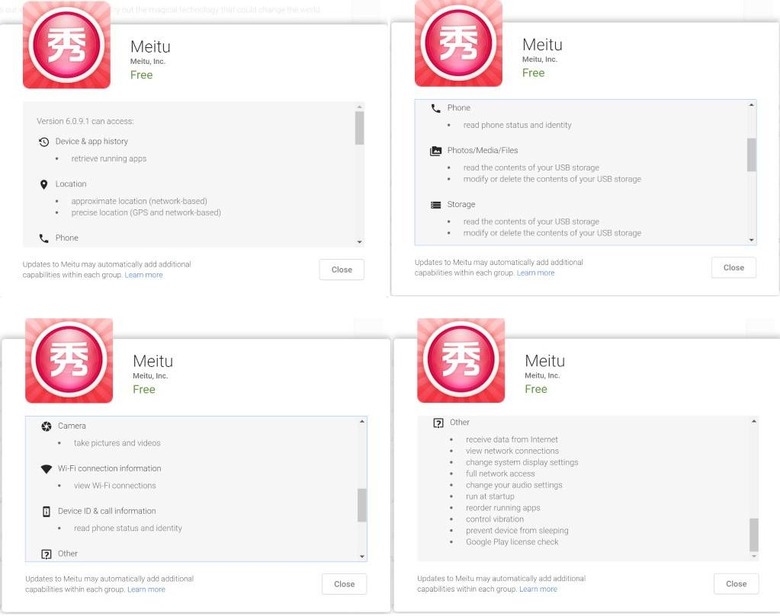
Also from FourOctets, permissions granted to the app at install are as follows – with descriptions. Watch out for that camera permission specifically.

Below you'll find a list of permissions the app is given when installed from Google Play. Similar permissions are given when the app is downloaded and installed on iOS devices. Apple-made iOS devices like iPhone or iPad are not immune to this situation – uninstall Meitu as soon as possible!
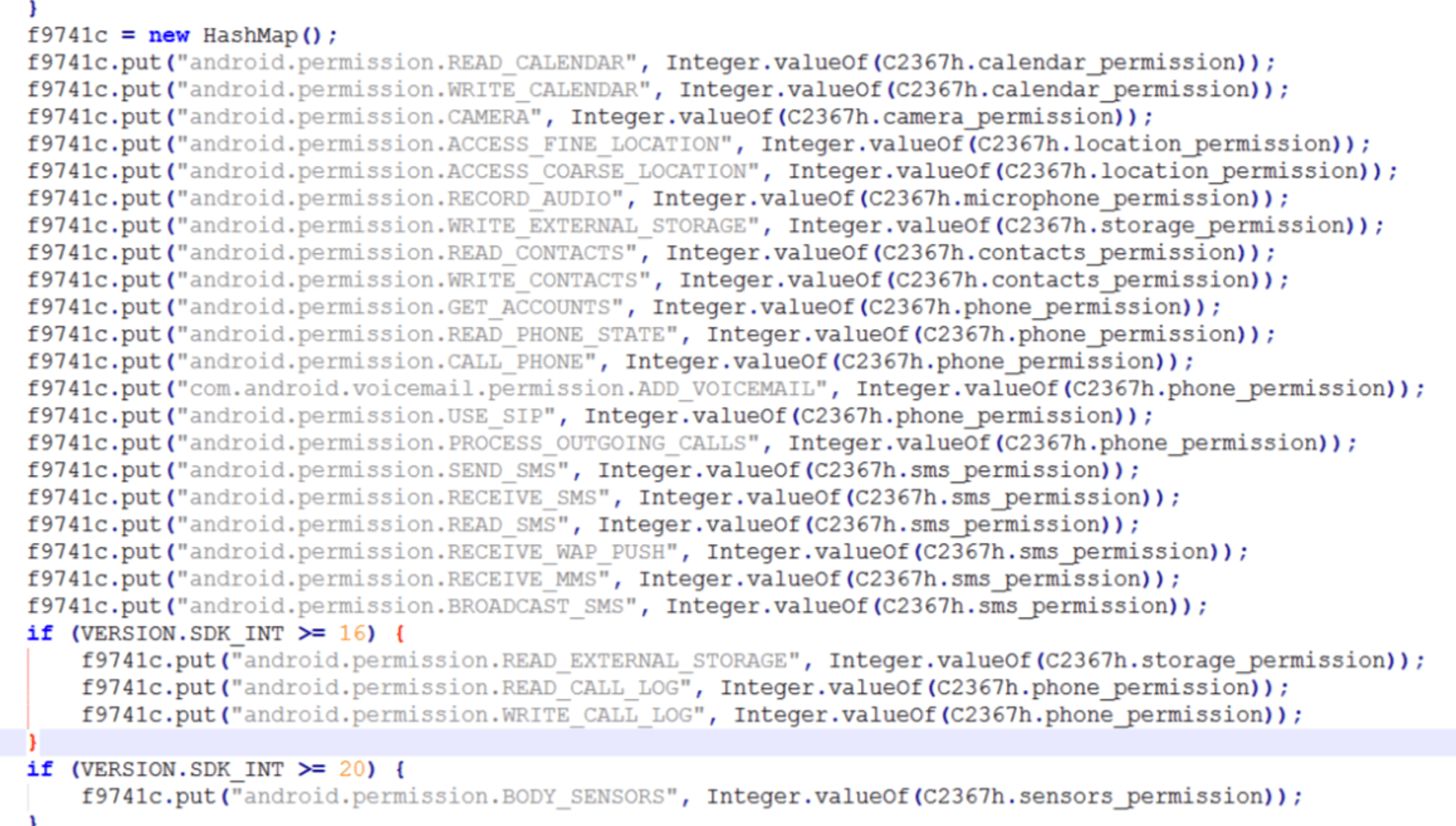
FourOctets continues with the following set of permissions the app seeks. Remember that even if you deny the app some of these permissions when installing the app, the app is still able to check your phone for IMEI and additional identification data. It's also able to send this information to a 3rd-party set of servers without your knowledge.
Investigation by SPNBMB suggest that the iOS version of this app is doing Jailbreak detection. That's essentially the same as root detection with the Android version of the app, and SIM status appears to be sent by the app as well.
Further information is being sought now. Stick around as we seek Meitu's word on this situation – whether or not they've been collecting this information over the past several years. If we find out more, we'll update this article.
UPDATE 1: A Meitu spokesperson provided the following statement to CNET this morning – "Meitu employs a combination of third-party and in-house data tracking systems to make sure the user data tracked is consistent. Furthermore, the data collected is sent securely, using multilayer encryption to servers equipped with advanced firewall, IDS and IPS protection to block external attacks." Meitu PR suggests that tracking services provided by the Apple App Store and Google Play are blocked, so they must use tracking code so they can track advertisements properly.
They also suggested that they're using a WeChat SDK for sharing content. This SDK apparently requests checks for jailbreaking and rooting of devices.
UPDATE 2: We asked Linares what his response was to allegations that this investigation was merely racism manifest as caution. He replied as follows.
"Regardless of where app and data is made or originated, your sensitive data is still being exfiltrated w/o your knowledge," said Linares. "Also companies in the US that we "trust" generally have more life long and sensitive data (ie social media sites). This is a relatively new company (to America) with little to no previous user data (and trust) from its users until now."
"I would have questioned it regardless of origin, the behavior is still questionable and users shouldn't accept this as normal."
Did you install and/or use Meitu recently? Have you noticed any suspicious activity on your smartphone and/or in any of your personal accounts recently? Let us know!