Apple AirTag Can Be Hacked But It's Not As Bad As It Sounds
Given its hard stance on security and privacy, it's really no surprise that Apple's latest accessories are being put under a microscope, both technically and even legally by the likes of Tile. The AirTag trackers, after all, are in a prime position to become spying tools and some hackers and security researchers seem to want to test whether that will indeed be the case. Based on a revelation over the weekend, the AirTag could indeed be reprogrammed but the process and the end result might not yet be worth the worry.
Like any electronic device, especially "smart" ones, the Apple AirTag has a microcontroller that orchestrates its activities. Those range from controlling battery and Bluetooth to determining what gets sent via its NFC radio. And just like any other computer, that microcontroller might be vulnerable to hacking, something that German security researcher and YouTube content creator Stack Smashing proved.
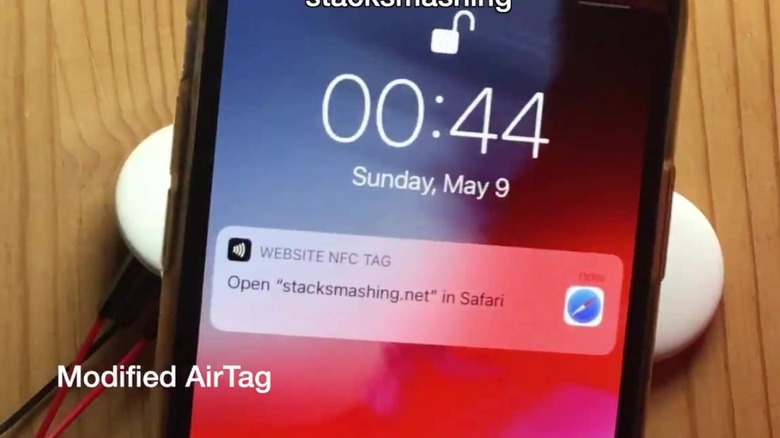
In a nutshell, Stack Smashing "hacked" the AirTag microcontroller to modify its firmware and make it do something other than what it is designed to. That, at least for now, meant linking to a different URL when an NFC-enabled phone "taps" the tracker. Normally, it would link to found.apple.com in order to initiate the Lost Mode process.
Built a quick demo: AirTag with modified NFC URL 😎
(Cables only used for power) pic.twitter.com/DrMIK49Tu0
— stacksmashing (@ghidraninja) May 8, 2021
This hack could be used to make phones go to some nefarious website but getting to that point might not exactly be straightforward. The security researcher hasn't disclosed yet the process but he admits bricking at least two AirTags to get there. Unless the tracker's firmware can be modified remotely over the air, the only way you'll get a hacked AirTag would be if you acquired it through other parties.
This AirTag hack might actually be less worrying than the debug menu that Apple may have accidentally left enabled before shipping the trackers. Fortunately, that might be something that is easily fixed with a firmware update, though that presumes that would-be hackers using it actually update the firmware in the first place.