Anonymous Ramps Pedophile Campaign With IP Honeypot
Hack collective Anonymous has ramped up its anti-pedophile campaign, reportedly tricking those attempting to browse clandestine sites hosting child pornography into accessing a service that would identify their IP address and, subsequently, identify and location. According to a statement attributed to the loosely-banded group, a custom Firefox button was developed and links placed to it – along with a fake Tor update message – on the "Hard Candy" and "Lolita City" sites offering the illegal content. Those who clicked it "would then be forwarded to our special forensics server and log the incoming IP and destination."
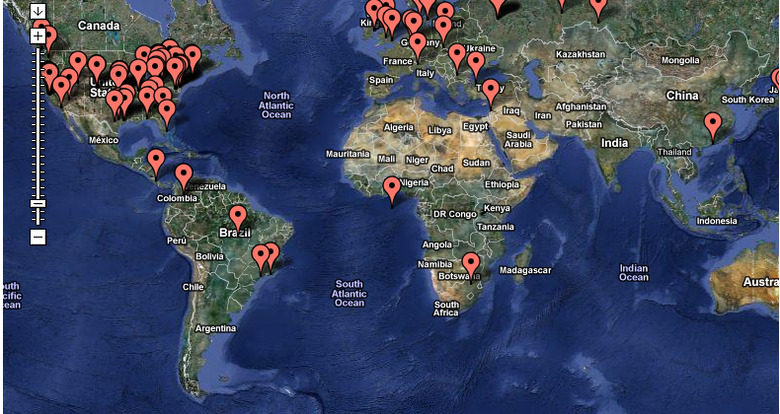
The operation, which Anonymous named "Paw Printing" in a reference to the "pedo bear" character, collected data for 24hrs, grabbing 190 user entries in that period. The map above shows the rough location of each entry, though the hack group also released the full IP logs.
Meanwhile, Anonymous also continues to target the hosts, and companies and individuals responsible for them, believed to be providing storage for the pornographic material. The sites are not publicly available, but instead use the Tor network – a system of encryption that is more commonly used to allow those in countries where internet access is blocked or severely curtailed to still get online – to operate in a so-called "darknets."