400 Qualcomm Snapdragon DSP Chip Bugs Put Phones At Risk [UPDATE]
The size of smartphones often belies the power they hold as well as the complexity of their construction. Phones may be said to come from this or that country or manufacturer but the truth is that different parts can be traced back to different sources and suppliers. All smartphones have many components in common, of course, and Qualcomm's Snapdragon processors have the lion's share of those. Unfortunately, that also means that when that particular chip turns out to have a vulnerability, it also puts the majority of the world's smartphones at risk.
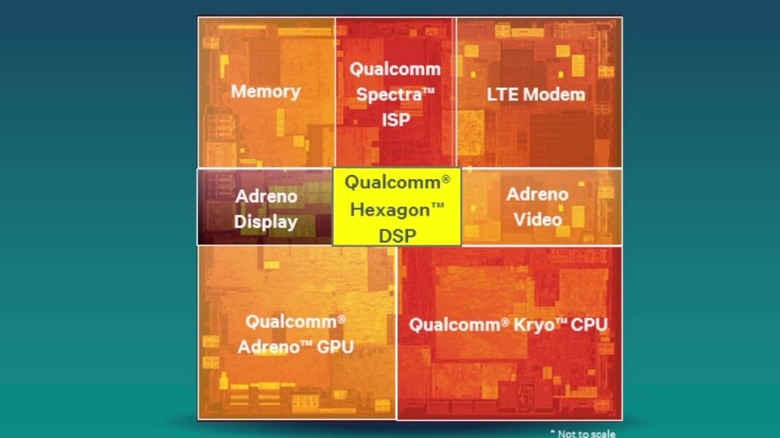
Bugs in software, especially those that directly control hardware, aren't uncommon, of course, but the staggering amount of vulnerability that the security researchers at Check Point discovered is particularly frightening. It reported no less than 400 vulnerabilities found in Qualcomm's Digital Signal Processor, which is markets as the Hexagon DSP, which is, in turn, found in all Snapdragon systems-on-chip and, therefore, the majority of smartphones in the wild.
You've probably had your fill of talk about Qualcomm's Snapdragon processors but the CPU, which Qualcomm refers to as its Kryo cores, is just really one of the many chips that work together inside the system-on-chip. Others, like the Spectra Image Signal Processor or ISP, deal directly with imaging functionality. The Digital Signal Processor, on the other hand, covers a lot of functions, from charging to audio to sensors and more.
That's precisely why this report of more than 400 vulnerabilities is quite worrying. Check Point Research explains that a compromised DSP could allow hackers to gain access to private information or use the device as a spying tool. They might even be able to render a phone practically useless by performing the equivalent of a denial-of-service (DoS) attack.
Check Point has already reported all these vulnerabilities to Qualcomm, device vendors, and the usual CVE publications. It isn't, however, disclosing the full details of the vulnerabilities until vendors are able to develop and roll out mitigations, hopefully quickly.
UPDATE: Qualcomm just sent an official statement regarding this vulnerability report:
"Providing technologies that support robust security and privacy is a priority for Qualcomm. Regarding the Qualcomm Compute DSP vulnerability disclosed by Check Point, we worked diligently to validate the issue and make appropriate mitigations available to OEMs. We have no evidence it is currently being exploited. We encourage end users to update their devices as patches become available and to only install applications from trusted locations such as the Google Play Store."