Do You Need To Connect To A VPN On Public Wi-Fi? Here's What You Need To Know
Free public Wi-Fi is everywhere; there are over 550 worldwide hotspots, by some estimates. It's rare to find a coffee shop or mall without one, and some countries (such as Singapore) make it freely available to everyone in public spaces. In some cases, even U.S. airlines offer free Wi-Fi to everyone, including economy passengers. However, being so accustomed to having a free public hotspot at their beck and call, everywhere they go, has made people a bit too trusting. According to a 2023 Statista survey, about 20% of respondents used free Wi-Fi to work remotely and make financial transactions — i.e., do highly sensitive things. If you've spent any time at all on the internet, you've likely been told that you should only connect to public Wi-Fi through a virtual private network (VPN) to protect yourself. But do you really need to?
As you've probably guessed by now, it's not a simple yes or no. In some cases, VPNs are necessary to protect yourself on public networks, even if marketing teams have a tendency to overhype their abilities, but the majority of the time, the reason to connect to one is not the one you probably think. We're here to get to the bottom of when a VPN is necessary on public Wi-Fi, and when it's not — and if it's not, what the real threat might be.
On secured networks, HTTPS is good enough
Part of the reason this myth is so persistent is that at one point it was true. Not too long ago, most websites were using highly insecure and unencrypted HTTP traffic, which meant hackers could read all the traffic on a public network like eating sushi off a conveyor belt. In addition to this, Wi-Fi network security used to be quite vulnerable to exploitation thanks to (now outdated) WEP and WPA protocols. VPNs keep you safe with a virtual private network, or an encrypted tunnel, which is why they were a really good idea when free networks were incredibly risky.
Unfortunately, VPN marketing still claims that without a VPN, there's no encryption taking place at all. Not so. When your browser connects to a website, it almost always uses HTTPS. HTTPS stands for Hypertext Transfer Protocol Secure, secure being the key word here. The secure part refers to Transport Layer Security (TLS), which encrypts your connection, keeping your browsing traffic between only you and the site you're visiting, even without a VPN. Almost 90% of websites use HTTPS encryption. It's vanishingly rare that you'll run into HTTP, and likely not for websites with sensitive information.
Further, Wi-Fi security standards have improved a lot as well. Now-commonplace WPA2 and WPA3 standards use advanced encryption that hackers cannot easily compromise. Assuming the Wi-Fi network you're connected to is using this modern encryption, a VPN is redundant. There are still ways that an encrypted network and websites with proper HTTPS encryption can be vulnerable, but we'll get to that later.
How to know you're secured with HTTPS
HTTPS is a must, no matter what you're doing, on public or private Wi-Fi. So how can you be sure the website you're visiting has an encrypted connection? If you're using a modern browser like Chrome, Safari, or Firefox, that's already taken care of on both desktop and mobile devices. All three (as well as Chrome alternatives like Vivaldi) will warn you before you try to connect to an HTTP website.
You should get into the habit of checking your connection status in the URL. On most browsers you'll see a padlock icon, indicating that the website you're connected to is using HTTPS. Click on the URL and you should see "https://" prefixing the website address. If its not using HTTPS, you'll see a "Not secure" label — and again, you would have received a warning before getting to that point (unless you've disabled that in your settings). Consumer Reports Security Planner has a helpful guide on how to enable HTTPS by default for all major browsers.
Again, few websites these days use HTTP, and most will either be places you won't visit on a regular basis or ones where using HTTP poses no risk. If a website you frequently visit is using HTTP (like, say, Gmail or Amazon), something is seriously wrong and you should avoid it until further notice. Never, ever send sensitive information over an HTTP connection. You'll be practically handing it over on a silver platter to any bad actors snooping around.
How to make sure your Wi-Fi is encrypted
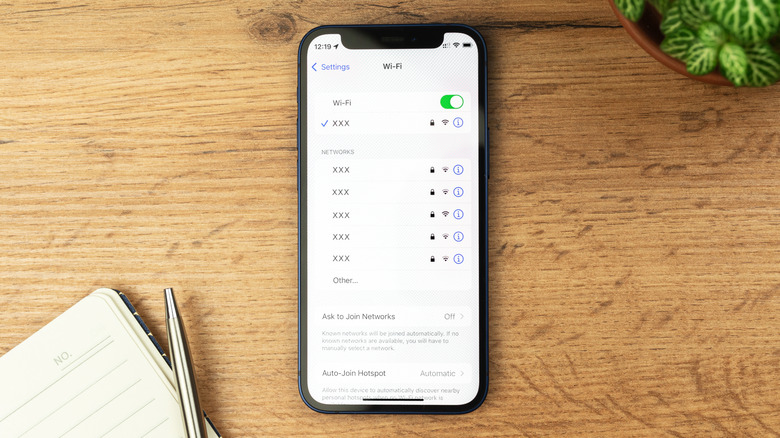
Much like HTTPS, all major operating systems provide convenient visual indicators to tell when you're on a secured or unsecured Wi-Fi network. Go to the settings on your device and find the Wi-Fi section. Similar to HTTPS, you should see a padlock icon if a network is encrypted. Open the Wi-Fi info (the circle icon with an "i") and you will see what encryption protocol your Wi-Fi is using. If you see WPA2 or WPA3, you can surf the web with peace of mind.
Your operating system will tell you if the connection you're using is not secure. On iOS, for example, the words "Weak Security" appear beneath a Wi-Fi network that doesn't use WPA2 or above — or even worse, the Wi-Fi might not be encrypted at all.Those older WEP and WPA protocols, you should avoid at all costs. Get into the habit of double checking that the Wi-Fi you connect to has a padlock before proceeding.
Part of the reason we're saying all this is to instill better digital vigilance. You should be mindful at all times of whether or not the websites and Wi-Fi you connect to are secure. Hackers rely on you blowing past all the warning signs. Just a teeny tiny bit of digital proactivity — taking two seconds to check for padlocks — goes a long way in securing your online presence
Does unsecured Wi-Fi require a VPN?
Here's where things get complicated. Even if you're connecting to properly configured HTTPS websites, you're not necessarily safe if you're still on an unsecured Wi-Fi network. Most Wi-Fi routers support WPA2 and WPA3, but if the person who set it up didn't enable it — or didn't configure it correctly — we've got a problem. If the Wi-Fi network doesn't require any sort of user authentication, it's likely not secured (or it's secured with WEP and WPA, which we've established are not safe).
The problem with unsecured Wi-Fi is very similar to the problem with HTTP. Since there's no encryption to scramble the data, it's passed along in plaintext, fully visible to any hacker who succeeds in compromising the network. It's called a Man in the Middle attack (MitM). Hackers in this position can steal your sensitive info and infect your computer with malware.
And while HTTPS is very secure, it isn't bulletproof. It lacks end-to-end encryption (E2EE), the most secure form of encryption out there. E2EE means the data is first encrypted on your device and only decrypted by the recipient. It's due to this lack of E2EE that you should stop using Telegram, or any private messengers that doesn't enable it by default. HTTPS can be intercepted because of how it encrypts data, and it has been many times in the past. So as far as using unsecured public Wi-Fi goes, you should probably use a VPN since that E2EE tunnel could secure your connection against MitM attacks.
Be wary of evil twin attacks
Unsecured Wi-Fi isn't actually the biggest threat out there. One computer hacking myth you need to stop believing is that hackers only ever do their work remotely. Realizing that people will trip over themselves to connect to free Wi-Fi, no matter how many red flags they have to blow past on the way, many hackers set up their own Wi-Fi network in a crowded public space. They make it look and act like a popular free Wi-Fi hotspot in the same area, let unsuspecting people connect, and then wreak havoc. This is known as an evil twin attack.
Once you've bitten the evil twin's hook, the hacker will try to intercept your traffic, trick you into logging in to fake websites to capture sensitive information, and push malware to your device. In some cases, hackers may even broadcast a Wi-Fi network that your device has already connected to, such as the one on your college campus, causing your devices to connect automatically without your knowledge.
So how do you prevent an evil twin attack? Avoid public Wi-Fi altogether, where possible. Using up your mobile data is a small price to pay for safety. Otherwise, double-check the hotspot names; evil twins will often have very similar (but not identical) SSIDs. If you're running into lots of network errors and SSL certificate warnings, that may indicate a hacker at work, so disconnect just to be safe. Evil twin attacks seem to be happening more often these days, so try to keep this one top of mind.
Be aware of known VPN vulnerabilities
VPNs themselves, regardless of which network they're connected to, may be vulnerable to a recently discovered vulnerability known as TunnelVision. In layman's terms, TunnelVision allows an attacker to see all of your internet traffic when you're connected to a VPN as if it wasn't encrypted at all. Unfortunately, this is not an issue with a simple fix, and it's especially concerning for public Wi-Fi hotspots since it requires the hacker to compromise the router — something that's more likely since public hotspot routers are often out in the open.
Not all operating systems are vulnerable. Android and Linux, for example, aren't affected, while Windows and Apple devices are. Some VPN companies have tried to address this vulnerability to their apps through features like a kill switch. You should research whether or not your VPN has found a solution for this issue. ProtonVPN, for example, says that Apple users only have to enable the kill switch feature to be protected.
Sadly, other vulnerabilities have been also discovered. Even more recently, security researchers uncovered a vulnerability affecting millions of VPN servers across the world. None of this is to say that you shouldn't use a VPN, but that you shouldn't put all your trust in one. VPNs have vulnerabilities just like anything else that runs on code, so it behooves you to keep up to date with the latest cybersecurity news and know what your VPN is doing in response to these threats.
Real reasons to use a VPN on public Wi-Fi
By now it should be fairly clear when you should use a VPN on free public Wi-Fi: when that Wi-Fi is unsecured. Having established that, there's another reason to connect to a VPN in public: data privacy. Since these are free hotspots, after all, the organizations running them might be making deals behind the scene to sell your browsing information to cover costs — or worse.
This isn't conjecture or speculation. Take LinkNYC, New York's free public Wi-Fi. Privacy advocates worried that user information gathered when connecting to a kiosk could be used to track people, particularly by law enforcement. Then CityBridge (the consortium running LinkNYC) was caught red-handed, admitting in its privacy policy at the time that it may share and sell some user information. Researchers in Montreal analyzed 67 public Wi-Fi hotspots of all kinds and found a staggering amount of data collection. We could go on, but in short, this happening everywhere.
While a VPN won't really keep you anonymous, it conceals your browsing activity from an ISP. A good VPN provider will often conduct independent security audits and open-source its code to prove it's not collecting or selling your info. You'll get no such guarantee from the random hotspot you connected to at the airport. Connecting to a VPN comes with minimal disadvantage too, since most use WireGuard, a fast protocol with low latency even on slow connections. Basically, you should use a VPN for any non-home Wi-Fi network because of data collection, if nothing else.
Should you use public Wi-Fi?
Having read all this, it's understandable to wonder if you should be using public Wi-Fi at all. It all depends on how risk-averse you are, what you plan to do on public Wi-Fi, and what alternatives you have at your disposal. If you have a decent cell phone data plan and you're not a heavy data user, then there's really no good reason to connect to a public Wi-Fi hotspot. Even if you are a heavy data user, going over on your plan will be way, way cheaper than picking up the pieces after a hacker compromises your digital life.
If you're just going to use the Wi-Fi for inconsequential things like browsing social media, watching streaming content then there's a lot less at risk. Just make sure the Wi-Fi hotspot is secured, double-check SSIDs in case there's a lookalike evil twin, and avoid logging into any login portals that appear at random. Taking the extra seconds to look for holes in your defenses goes a long way.
If you're going to do anything sensitive (like accessing your email or opening your bank account app) then consider either doing it later when you're on more trustworthy Wi-Fi network, or accessing these things via your cell phone data plan. If you absolutely have to (such as being in a foreign country) then connect to a VPN just to be safe.
Ways to protect yourself on public Wi-Fi
If you're going to bite the bullet and connect to that free hotspot, take some precautions to reduce the risk. We've already covered the biggest ones: don't log into any random portals that pop up, connect to a VPN on unsecured networks, etc. On a secured network, use a VPN to protect your data privacy. What else can you do?
One of the most important things you can do is use apps and services that support E2EE by default. Instead of Facebook Messenger and Instagram, try other Messenger app alternatives. If you own an Apple device, set up Advanced Data Protection (effectively E2EE) for your iCloud. E2EE is the best choice in any situation because the data is encrypted before it leaves your device, making it almost impossible for a hacker to compromise sensitive information even on an untrustworthy Wi-Fi connection.
If you're going to be in a foreign country, consider getting an eSIM card with a high data cap. It's not as expensive as you might think. Using Ubigi as an example, a 10GB plan for 30 days in Mexico might cost you as little as $24. eSIMs give you an active data plan that works the second your plane touches down in your destination country. If you've got enough data, you'll never even have to think about public Wi-Fi.
Avoid free VPNs
You can scroll for ages through all the free VPN services on the Google Play Store or Apple App Store — we strongly recommend against any of them. Think about it. How does a free VPN earn money? It can serve you ads inside its app, but you're only going to be there long enough to hit the connect button. Most go to town collecting and selling your data. And many use weak encryption protocols, offering slower speeds, fewer servers, and fewer connection options, to boot.
You don't have to spend big for a paid option these days. The best VPN services available run for as little as $2 a month in some cases. That's less than the price of a cup of coffee a month for unlimited bandwidth, a huge number of servers, built-in ad blockers, and whatever else your VPN service provides. Your Netflix subscription starts at $7.99 a month and that supports only two devices, the lowest resolution, and includes ads; if you can justify Netflix, you can justify a VPN.
If paying for VPN is completely out of the question, at least use one that you really can trust, like ProtonVPN. ProtonVPN offers a free VPN service for a single device with a limited number of servers. ProtonVPN uses this to promote its paid VPN, hoping you'll subscribe if you like the experience. So in a sense, it's subsidized by regular paid users and suffers none of the privacy infringements that a free VPN might.