Stop Signing Into Websites With Google And Facebook And Do This Instead
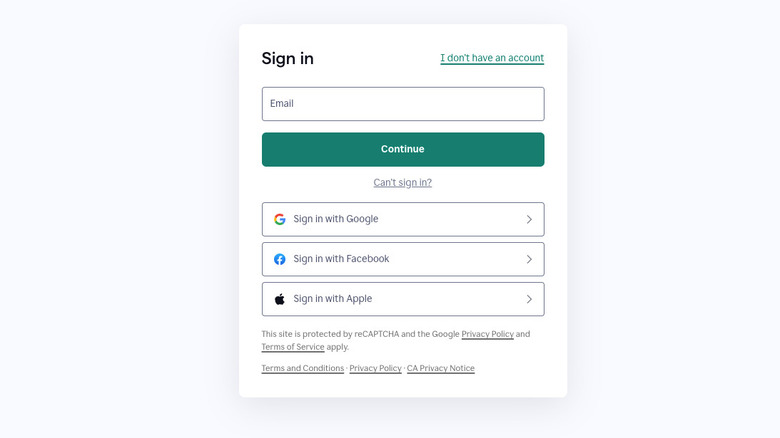
On most major websites, you're bound to see a handful of familiar icons under the login credential fields. Likely, an option to sign in to that particular website via Google, Facebook, Apple, and other platforms. Once you've tasted this forbidden fruit, you're hooked, and it's hard to resist the allure when the option presents itself on other sites and services. It's effectively a one-click login every time from then on out, arguably the fastest possible way that there is to log in, period. The lack of convenience becomes painfully noticeable any time a website doesn't support it. However, it may be time to stop using this convenience altogether.
For reference, this type of login is known as SSO, or single sign-on. Rest assured, clicking on a Google logo doesn't inherently let a hacker steal your Google account or something of that nature. Rather, there are quite a few practical and logical reasons — some with security implications — as to why it might be in your best interest to avoid SSO in favor of passwords. With that in mind, let's discuss the problems with SSO, and what you should do instead.
How SSO works
SSO effectively creates an account via Google (or any other account you use), minus the username and password. In place of credentials, Google authenticates your identity via an access and ID token, granting entry. You can give permission to provide the information the service needs, and nothing else; permissions, depending on which account SSO you use, can be modified in the future without revoking login access. Future visits will use the same token.
You may have noticed that anytime you accidentally try to login with an email, the service redirects you to use the SSO sign in button. This is proof that a bad actor wouldn't be able to compromise that account with a typical brute-force password attack; they'd have to break into your SSO account instead. If you choose to ditch your password in favor of a passkey, the threat of a compromised password is off the table altogether.
SSO arguable replaces whatever weak security a website has with Google's top-of-the-line security. You also potentially have more control of your SSO account's data, since you grant permission for the website to see only what you wish it to see and can unlink that data at will. Finally, SSO would allow you to make multiple accounts on the same website (in the rare situation you need to) with greater ease; you just click the SSO button for Google, Facebook, and others separately. But that convenience and security comes with some caveats that aren't immediately obvious.
Your SSO account is the linchpin of your online world
The biggest problem is that using SSO login as a primary means of access to your accounts raises the stakes to a dangerous level if you ever lose access to that main SSO account. If someone were to compromise your SSO account — let's stick with Google, for the sake of example — they wouldn't just gain access to your email and drive; they would have access to every SSO-enabled account under the wing of Google, too. You're effectively giving them access to multiple accounts, possibly all of your digital life.
Take the Facebook security breach in 2018 that affected 50 million users, which indirectly affected SSO, too. It's hard to know how many people were negatively impacted by abuse of those SSO logins following the breach, but you see the risk. Regardless of how your account is compromised, your SSO login will likely be a casualty.
Think of how that impacts the incentives for hackers, too. Instead of going after your smaller accounts, they are driven to put even more effort into the white whales of Google, Facebook, Microsoft, Apple, and Amazon. Data seems to agree that these linchpin accounts are under increasing fire. Forbes recently reported that phishing attacks on Google accounts — and others — having increased 243% in early 2024. It might be only a matter of time before you're caught in a security breach that makes you wish you'd never used SSO in the first place.
You're giving login credentials to a random company
There's an even greater threat that you may not have considered: the company behind the SSO account. Some major companies that provide SSO login have a long history of abusing user data and privacy. Google recently paid out a settlement for looking at your incognito browsing data in Chrome. This stuff happens day and night, so why trust a company that demonstrates utter disdain for your personal info with a sensitive login?
It's unlikely that Google is going to use that token against your wishes and without your knowledge. However, you should be aware that your data is often not end-to-end encrypted (E2EE), which means only you can access your data. The lack thereof, like that of Telegram messenger's default chats, should be concerning. In the case of Google, data is encrypted server side and at rest, not E2EE. That means (at least in theory) that an employee insider with nefarious intentions could access your account.
To give one example, it was recently discovered that a Google employee was stealing intellectual property (via NBC News). Naturally, intellectual property doesn't include user information, and authorities believe it to be PRC-backed espionage, but the point still stands. Google employees could be a much greater threat your logins, perhaps especially with all the massive tech industry layoffs in recent years. If not disgruntled employees, then at the very least a lack of E2EE cracks a door for hackers during a breach.
Account access depends on the SSO account
Another possibility is that your SSO account could at any time (and for any reason) lock you out. Being locked out will most likely prevent you from logging in to any websites tied to the SSO feature, even beyond insider or hacker security breaches. You'd be shocked how often people are completely locked out of their SSO accounts (often completely at random) for alleged violations of the TOS. Business Insider reported on how this happened to some Google users, and how in some cases it was impossible to recover their accounts. Make no mistake, this could happen to you, and you'd have just as little recourse. Losing account access can happen for many reasons, from forgetting your password, to losing your 2FA device, to an account being deleted for inactivity.
The point is that if you suffer account lock-out, you'd have to say goodbye to all your SSO sign-ins. The risk of losing access is low if you have good digital hygiene and secure your accounts immediately after a breach. However, there's just no telling if and when such a tragedy could strike, and how much you stand to lose. One thing's for sure: if that day comes, you'll be hitting yourself for prioritizing a few seconds of convenience over security.
Login habits could be sold to advertisers
The last issue has nothing to do with account access, but rather, what the company behind the SSO account does with your data. Think about it. When you default to SSO with Google, you're telling them about potentially dozens of websites and services you use, websites and services they may have otherwise never known were connected to you.
Major megacorps like Google and Facebook swear up and down in their privacy policies that they never, ever sell your personal info. Yet year after year, each of them is caught knuckles-deep in the cookie jar, gets a slap on the wrist, and then does it again.
Had you used an email and password combo sign-in instead of SSO, you'd only have to worry about the privacy practices of that one company. If you don't trust that company, there's nothing stopping you from creating a dummy email to open the account while preventing the brand from selling you out. Regardless, you have a lot more control of your data simply by avoiding SSO.
A password manager doesn't lock you out of accounts for good
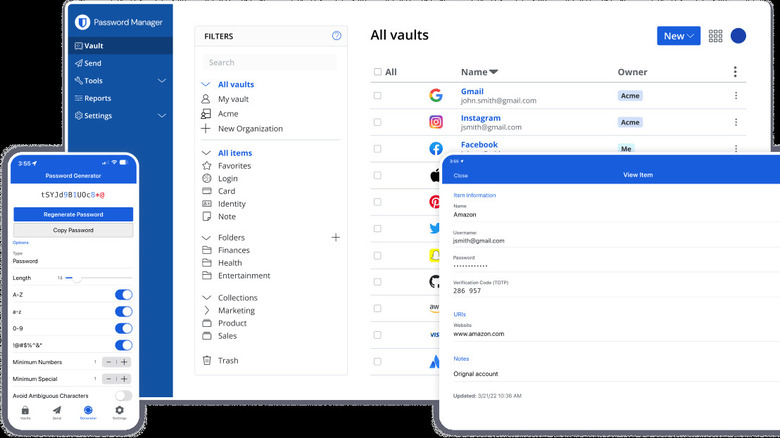
If any of the above points concern you, it's time to ditch SSO in favor of a password manager. A password manager allows you to store all of your passwords in a secure vault, locked down with a single, strong password; you no longer have to remember secure passwords for multiple sites or risk using the same one on all of them (please don't do that). Password managers often support storing 2FA codes, passkeys, backup codes, and even payment options in one place. One of the major advantages they have over SSO is that password managers don't lock you out of your accounts should you lose access to the password manager itself.
With a typical login (as in, not SSO), the password is immaterial. You can usually recover the account with your email address, and most accounts these days give you recovery or backup codes — extra peace of mind in case you should lose access to the connected email address, too. That's yet another point for username-password accounts over the SSO variety.
Limit what hackers can do if they compromise one account
Another benefit of avoiding SSO is account compartmentalization. As mentioned previously, if your SSO account is compromised, all the accounts linked to it are potentially compromised as well. It puts an incredibly large burden on that one account, requiring you to be extra cautious with security and incentivizing bad actors to target it. There's a longstanding saying in the cybersecurity community: it's not if you're hacked, but when. It doesn't matter how good the lock on the door is, because someone will find a way to bypass it.
In a case of using a username-password combination stored in a password manager, there's less spill-over if one account goes down. A unique password for one site can't be used for another, compared to an SSO account where the hacker needs only click on the Google SSO icon wherever they find it. Damage control after an account breach with the former will be much less devastating, since, well, much less of your online life has been sullied.
Log-ins are (virtually) just as easy
The primary benefit of SSO is convenience. Going back to manually entering a username and password becomes tedious when you get used to logging in with a single click. Especially since, without SSO, it would be a different login for every site.
Luckily, most password managers on the market have a browser extension that enables automatic autofill for credentials and 2FA codes. To further expedite the process, some (like 1Password) will hit the enter key for you so it literally becomes a one-click process. Of course, some websites have a janky input field that makes it so the 2FA doesn't go in right, or it's hard to erase when the code times out. Still, it's preferable to make that tradeoff of a few extra frustrating seconds if that means keeping your accounts secure.
Logins are easier still when you introduce passkeys into the equation. Passkeys use biometrics to quickly and securely log you in with a key stored on your device, no username or password required. Without a password manager, the passkey is stored on a single device and you have to create a new one for additional devices. But if you switch to a password manager, it will likely support passkey storage. Passkeys then sync across all devices and work whether you're on desktop or mobile.
You get extra security features to lock-down accounts
SSO is only an alternative to logging in; there are no additional security features for you to customize. As a result, you're stuck with whatever security implementations of SSO the account offers, be they good or bad. Password managers may also be a single point of failure, but at least they go above and beyond to secure your account and restrict access.
Let's use Bitwarden as an example. First, it's E2EE, a staple of any good password manager; only you can access your passwords and anything else stored in your secure vault. It lets you adjust the KTF security iterations; in layman's terms, strengthening the encryption at the cost of login taking a second or two longer. You can enable two-step login, which prevents access even if someone were to obtain your master password. You can set exactly when your vault times out and locks itself, when it logs you out, and if local system biometrics are allowed to access it. You can even have it clear your clipboard to prevent copied passwords from lingering in your clipboard history.
The list goes on. If it weren't clear already, password managers distinguish themselves by making your stored credentials as difficult to steal as possible. You can't always say the same for SSO providers.
Create a second 2FA account for more security
Even with all those security features, it's understandable that the more paranoid out there would rather not put all their eggs in one basket. For an extra layer of protection, it's recommended to keep the password separate from the OTP authentication codes. Otherwise, someone would have full access to all your accounts with your password manager alone.
Every major company has its own standalone OTP code generators; Microsoft, Apple, Google. In the spirit of compartmentalization, however, it's good practice to avoid using an authenticator made by the company that makes your email and operating system. Plus, some — like Google Authenticator — do not sync with the cloud, making them a tad less convenient to use.
My recommendation is Ente. The app is cross-platform, fully open-source, and chock full of security features to keep those 2FA codes out of the wrong hands. It's free to use and makes it easy to import tokens from other apps. As runner-ups, I suggest either Bitwarden Authenticator or Aegis. Neither support syncing your vaults at the time of writing, but that may be preferable to some people; if you keep your 2FA codes offline, you create a much larger hurdle for a hacker to clear.
Use Bitwarden as your password manager
My personal daily driver is Bitwarden. I've used it for about four years. It's free to use, open source (which means anyone can look at the code for vulnerabilities), cross-platform, and has received positive third-party security audits from respected cybersecurity firms like Cure53. Bitwarden lets you store unlimited passwords and passkeys on as many devices as you'd like, and for the premium version (only $10 a year) you get 2FA codes, file attachments, and more.
On the App Store and Google Play Store, Bitwarded maintains 4.0 out of 5 (and above) ratings. I wouldn't say it's cutting edge when it comes to features, but is neck-and-neck with other major players like 1Password, DashLane, and LastPass. The built-in password generator is one of my favorite parts of the app; you can define exactly which types of characters you want, how long you want the password to be, and make the password easier to type out by using a passphrase or avoiding ambiguous characters.
Bitwarden can be strictly for passwords only, or it can hold everything. Thanks to the handy browser extension, you can use it as a more secure way to autofill credit card info, passport and driver's license details, and even social security numbers. Bitwarden makes it easy to securely share passwords with people you trust, or send sensitive information without relying on a sketchy Google Drive link. Suffice it to say I'm a very happy customer — and a very protected one, too.