Flights, Banking, And More Brought To Standstill In Global Outage: Here's What Went Wrong
On July 19, a large-scale series of interruptions and outages struck Windows OS-based computer systems all over the world. Multiple major airlines, including Delta, United, and American Airlines were forced to ground flights when their computers suffered complete blue screen lockups. Similar hitches were experienced by several major banking institutions, hospital booking systems, television networks, and more. A fix was promptly deployed, but the severe damage and setbacks caused by this sudden outage caused some concern on the state of the global wireless grid.
As was revealed shortly after the incident, this massive outage was not the result of a deliberate cyber-attack, but rather due to a flawed update released by global cybersecurity firm CrowdStrike. The CrowdStrike software in question is widely utilized by many professional users of Windows operating systems in the aforementioned industries to protect their respective systems. So, when the update rolled out and caused an error, all of those users suffered simultaneous stalls.
1. All too often these days, a single glitch results in a system-wide outage, affecting industries from healthcare and airlines to banks and auto-dealers. Millions of people and businesses pay the price.
These incidents reveal how concentration can create fragile systems.
— Lina Khan (@linakhanFTC) July 19, 2024
In a post on his personal X (formerly Twitter) profile, CrowdStrike CEO George Kurtz said that the company "is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This is not a security incident or cyberattack. The issue has been identified, isolated and a fix has been deployed."
The CrowdStrike chief's subsequent apology wasn't particularly well-received, however, owing to the mute tone, especially in the context of the disruption's global scale.
How the cascade effect kicked off
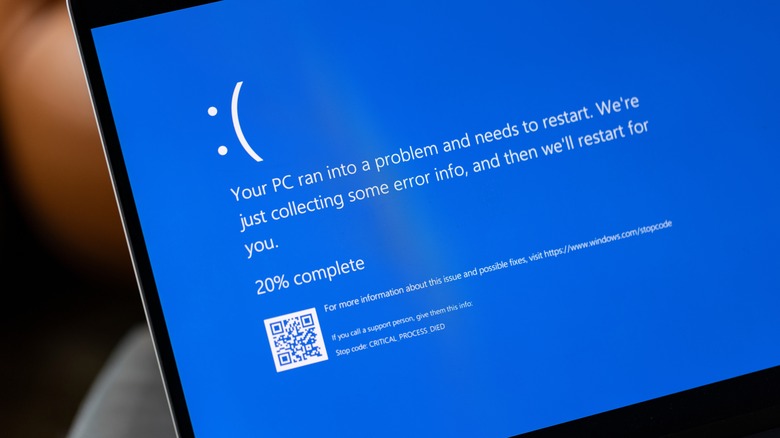
The havoc was stirred when CrowdStrike started seeding a sensor configuration update targeting its Falcon platform on machines running Windows 7.11 or a later version. The update kickstarted what the company calls a logic error, which eventually triggered the infamous blue screen of death error (BSOD) on Windows machines, leaving them non-operational.
The specific nature of the problem is related to Microsoft Azure, a cloud computing management system offered by Microsoft and utilized by various businesses. When the flawed CrowdStrike update rolled out, users of the Azure framework experienced a severe error that completely locked up all connected systems.
With both Microsoft and CrowdStrike's work, most of the affected systems have been successfully brought back online. However, for some of the affected systems, the lockup has been so severe and widespread that physical shutdowns and reboots were required in some cases.
In the wake of the widespread service interruptions, Microsoft released a recovery tool with two separate routes for wrestling back normal system functionality. Notably, the faulty CrowdStrike update targeted only about 8.5 million Windows devices, which is less than 1% of the total install base of Microsoft's operating system. However, even that short-lived outage for only a small share of active Windows machines was enough to deal financial damage worth an estimated one billion dollars, or more.
How the CrowdStrike outage raised cybersecurity alarms
When the widespread Falcon update outage first gained widespread media attention, the company quickly clarified the BSOD woes plaguing Windows machines were not due to a cyberattack. However, the sheer scale of the disruption opened an opportunity for bad actors to take advantage of the panic that ensued.
In an official blog post, CrowdStrike revealed that it has received reports of bad actors trying to trick users posing as cybersecurity customer support. In some cases, the malicious entities were also trying to pass themselves off as cybersecurity experts. The most dangerous outcome, however, was hackers attempting to sell fake tools that would supposedly help recover systems hit by the BSOD issue.
⚠ As expected, the incident with #CrowdStrike has been exploited to distribute malware.
🎯 In our example, an archive containing #Hijackloader, which delivers #Remcos to the infected system, is downloaded into the system under the guise of a #hotfix.
💢 The name of the ZIP... pic.twitter.com/BieB7LcTqe
— ANY.RUN (@anyrun_app) July 20, 2024
In another update, the company also highlighted a whole bunch of packages and websites with the name "crowdstrike" to avoid scrutiny and trick users. Some samples of such malicious software tools include "crowdstrike-hotfix.zip," "fix-crowdstrike-bsod.com," "crowdstrikeupdate.com," and "crowdstrikefix.com," among others. The Department of Homeland Security also raised the alarm, noting that the agency had "observed threat actors taking advantage of this incident for phishing and other malicious activity."
Malware researcher Arnold Osipov also spotted a PDF file trying to pass off as an official remedy guide from CrowdStrike. In reality, it was trying to dump malware on the unsuspecting victim's PC. The zip package described above is said to deliver HijackLoader payloads, according to the folks over at ThreatMon, targeting customers in Latin America. So far, we haven't come across any verified reports of malicious websites and packages dealing any damage to organizations that were hit by the CrowdStrike outage on their computing infrastructure.
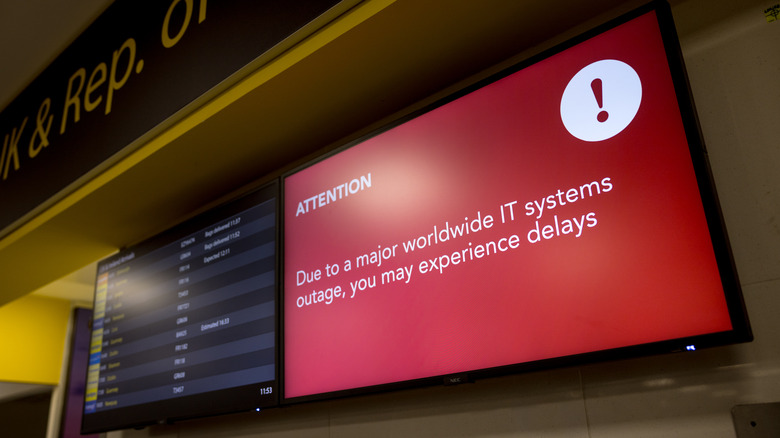
A heavy hit on airline services
Airline services were the hardest hit, with Delta being the biggest casualty. The company was also on the receiving end of heat from U.S. Transportation Secretary Pete Buttigieg, who lambasted "continued disruptions and unacceptable customer service conditions" by the airline. The aftermath of the disruptions caused by the CrowdStrike spilled well into Monday, drawing a stern warning from Buttigieg.
Delta must provide prompt refunds to consumers who choose not to take rebooking, free rebooking for those who do, and timely reimbursements for food and hotel stays to consumers affected by these delays and cancellations, as well as adequate customer service assistance.
— Secretary Pete Buttigieg (@SecretaryPete) July 22, 2024
According to data compiled by FlightAware.com, the company canceled hundreds of flights on Monday, with the total tally standing well over four thousand by the safest estimates. Delta, on the other hand, has promised a full waiver for all flight bookings made in the July 19-23 slot, as long as the rebookings are made before July 28.
Aside from Delta, the airlines worst hit by delays and cancellations over the course of the past three days include United, Endeavor Air, Spirit, China Eastern, American Airlines, Ryanair, easyJet, Republic, and WestJet, among others. Internationally, Greece's Aegean Airlines, Air India, IndiGo, Akasa Airlines, and SpiceJet in India, Air France, Spain's Binter, Australia's Jetstar Airways and Qantas, Dutch airline KLM, Lufthansa, Eurowings, Singapore Airlines, Portugal's Tap Air, Turkish Airlines, Swiss International Airlines, and more were all hit by service disruptions.
The FAA is working closely with airlines impacted by a global IT issue. This timelapse depicts air traffic recovering after airlines requested FAA assistance with ground stops this morning. Contact your airline for more info and monitor https://t.co/smgdqJN3td. pic.twitter.com/inRTK6ovTI
— The FAA ✈️ (@FAANews) July 19, 2024
Indian airports were also hit, where whiteboards and hand-written boarding passes were observed. Notably, the disturbances in airline services were mostly restricted to companies operating in the West, especially in North America, Europe, and some portions of Australia. According to experts cited by ABCNews, China dodged the bullet because businesses there rely on local anti-virus tools, while a healthy bunch of unaffected companies in Asia remained unscathed because they simply couldn't afford the tools, the likes of which are offered by CrowdStrike.
The impact on emergency services
One of the scariest aspects of the service disruption was how it affected emergency services — not just for healthcare appointments, but for emergency services, too. "In Alaska, both non-emergency and 911 calls went unanswered at multiple dispatch centers for seven hours," says USA Today. The report adds that agencies across seven American states witnessed such systemic disruptions. To handle the situation, some personnel were shifted to stations where the emergency services were intact in order to handle the increased influx of calls.
Since the digital infrastructure had failed, at locations such as Noble County in Indiana, emergency responders handled calls in the early morning hours and took notes on pen and paper. Wherever possible, call routing was also put into practice. In New Hampshire, a small portion of the 911 services were also down briefly, but they were quickly restored. The computerized 911 dispatch center was also affected by the CrowdStrike outage in Phoenix, with the local police department asking citizens to stay on the line if their call is put on hold. The FCC also confirmed via a post on X that it was aware of service issues plaguing the 911 emergency hotline.
In addition to emergency services, driver services were also impacted. According to CNN, driver's license and service centers across Texas, Tennessee, North Carolina, and Georgia were hit by outages that hindered their ability to dole out facilities such as processing payments and handling requests related to driver's licenses and vehicle plates.
Border security and immigration delays
In addition to the obvious commercial and industrial endpoints vulnerable to the outage, the CrowdStrike fiasco also slowed down cross-border operations, as well. The CBP One app, developed by the U.S. Customs and Border Protection agency, also ran into technical issues. Newsweek reports that users were no longer able to see the waiting times for different application stages. The agency also shared in a statement that the mobile application was facing "processing delays."
Another report from NewsNation mentions that the CrowdStrike outage has hit "all Customs and Border Patrol laptops and workstations, along with system applications." Due to the systematic issues, some people waiting to cross the border in the El Paso sector have been hit with delays as lengthy as three to four hours. Peace Bridge in Buffalo, New York, reportedly suffered backup issues as well.
The border crossing at the San Ysidro pedestrian line was also affected, while travelers destined for the Tijuana airport and Cross Border Xpress were told to arrive earlier than their planned schedule, according to a report by The San Diego Union Tribune.
On July 19, U.S. Customs and Border Protection (CBP) is experiencing processing delays due to the global technology outage. We will continue our work to restore our systems to full capacity and provide updates as they become available. pic.twitter.com/mPjMdByNjp
— CBP (@CBP) July 19, 2024
Per the Associated Press, long delays were reported at the Ambassador Bridge and the Detroit-Windsor tunnel, which is near the U.S.-Canada border, and falls under the jurisdiction of the Windsor police. Even passengers who were a part of the "Trusted Traveler" program developed by the U.S. Customers and Border Protection ran into delays. In Bangkok, the border control systems across two airports were also reported, with similar problems raising their head across Singapore and Malaysia.
Non-quantified hit on the banking sector
Another expected victim of the CrowdStrike outage was the banking and trade segment, mostly because involved parties readily lap up any enterprise-grade cybersecurity solution to keep them safe from hackers. Among the high-profile victims of the service outage were giants like Wells Fargo, Bank of America, Capital One, Chase, TD Bank, TD Ameritrade, Charles Schwab, and Fidelity Investments. Per data recorded from Down Detector, Arvest Bank was also on the list of banking entities affected by the CrowdStrike outage, according to the Austin American Statesman.
CNN reports that Australia's Commonwealth Bank experienced service disruptions, alongside ANC and Westpac. ASB Bank in New Zealand also reported experiencing service issues. The Bank of Israel, Capitech in South Africa, and Barclays in the United Kingdom also confirmed operational hiccups.
Please see below for information on impacts to our services experienced today. pic.twitter.com/4XXt5W7Nt4
— TD (Canada) (@TD_Canada) July 19, 2024
So far, no reports have emerged where bad actors took advantage of baking service disruptions to deal any kind of meaningful damage. However, that doesn't mean they were not trying. A similar warning was also issued by the Australian Cyber Security Center and the UK's National Cyber Security Centre. The New Zealand Herald also reports that attempts to capitalize on the outage were also discovered by the country's premier cybersecurity agency.
The toll on food and freight services
The CrowdStrike outage also affected the food supply chain, although the impact was not as well pronounced as the healthcare and travel industries. Among the food and beverage giants affected the service downtime were McDonald's and Starbucks. In Japan, roughly 30% of McDonald's outlets were shut down, an event which also took a toll on the company's share prices in the country, according to Bloomberg.
【お知らせ】
全国の多くの店舗で一時的に営業を停止しております。
お客様にはご迷惑をおかけして大変申し訳ございません。— マクドナルド (@McDonaldsJapan) March 15, 2024
Another food and beverage franchise hit by the CrowdStrike update mess was Starbucks. According to USA Today, the official mobile app was non-functional for customers, and it seems the credit card point-of-sale system also ran into issues. Some stores reportedly resorted to accepting only cash for orders. "Starbucks is among those companies experiencing impacts due to a widespread third-party systems outage, resulting in a temporary outage of our mobile order ahead and pay features," a Starbucks executive was quoted as saying.
In addition to the food supply chain, the system outages also took a toll on the goods and transportation segment, halting movement in the U.S., as well as in international ports. "Thousands of flights were grounded or delayed at the world's largest air freight hubs in Europe, Asia and North America," says an NBC report. UPS took a hit in the U.S. as well as Europe, while FedEx also went into contingency mode. Union Pacific was the only railroad freight entity that reported operational hassles following the CrowdStrike-triggered outage.
The healthcare industry was equally hard hit
The CrowdStrike outage was also a wake-up call for the global healthcare industry. "These disruptions are resulting in some clinical procedure delays, diversions or cancellations," notes the American Hospital Association, adding that emergency call centers were also affected by the CrowdStrike outage.
A resident doctor at the University of Louisville told Fortune that "every single computer was down" at the school's clinic, blocking access to everything from patient records, to drug monitoring and digital prescription tools. Global Data reports that over 40,000 computers were offline at Providence Health. Notably, CrowdStrike says it is part of over a million healthcare endpoints in the U.S. alone, and serves over 100 organizations.
BILH locations are open & providing patient care. Please arrive as scheduled for any appointments unless you hear from a member of your care team. Our teams are working to resolve the impacts of a global technology outage and there may be delays. We appreciate your patience.
— Beth Israel Lahey Health (@bethisraellahey) July 19, 2024
Boston's Mass General Brigham canceled "all previously scheduled non-urgent surgeries, procedures, and medical visits," keeping only the emergency units functional, but at a much slower functional place, according to CBS News. North Carolina's Core Health network nixed surgeries and treatments, and Michigan-based Corewell Health alerted patients about appointment delays. Labs like Labcorp also felt the impact, impeding delivery of testing reports to patients and doctors.
— Kaleida Health (@KaleidaHealth) July 19, 2024
Epic Systems, one of the biggest names in the electronic health record platform segment, also reported running into technical difficulties accessing its systems, according to Bloomberg. "In the UK, National Health Service general practitioners had trouble accessing scans, blood tests, and patient histories," adds the report.
Procedures that required the use of anesthesia were put on hold at New York's Memorial Sloan Kettering Cancer Center, and elective procedures were canceled at University Hospital Schleswig-Holstein in Germany. As well, self-check-in appointments also ran into trouble at the Parisian Saint-Joseph hospital, while access to imaging and test data was out of bounds for some experts at the London Museum Practice.
The aftermath of the CrowdStrike outage
In the wake of service disruptions that sent ripples across the globe, serious questions have been raised about cybersecurity and industry risk factors. One of the questions was about the concentration of technical prowess in the hands of a few corporations, which echoes how Big Tech currently operates across verticals like computing, mobility, consumer electronics, and social media. "Millions of people and businesses pay the price. These incidents reveal how concentration can create fragile systems," FTC chair Lina Khan shared on X.
Another pertinent question was that mass service disruptions across crucial segments such as banking, emergency response, healthcare, and travel, don't always come courtesy of cybercriminals or foreign adversaries. Sometimes, serious upheaval can be generated by a widely-adopted tech stack. In this case, the security tool offered by CrowdStrike, and the underlying execution platform by Microsoft courtesy of its Windows operating system.
In the wake of the incident, demands for accountability have been made, and the calls are being raised right in the House corridors. In a letter, Republican lawmaker Mark E. Green, who is also Chairman of the Committee on Homeland Security, and Andrew R. Garbarino — Chairman of the Subcommittee of Cybersecurity and Infrastructure Protection — have asked CrowdStrike chief Kurtz to testify regarding the incident.