Jeep Hacking Done On Willing Participant
Today's big news about a Jeep being "hacked" from a remote location was done on a willing test-dummy of sorts. The man – Andy Greenberg – writes for Wired magazine, and agreed to be part of this hacking experiment over the past year. Their work – these hackers, that is to say – was indeed a test, and not entirely malicious, but that's no reason to stop the panic. The hack they performed was real, and it really COULD send signals to this vehicle's dashboard via the internet.
These hackers could just as easily be called researchers. Researchers Chris Valasek of IOActive and former NSA staffer Charlie Miller. Together they've worked with a variety of cars to check vulnerabilities in their own time.
They've successfully hacked the Uconnect smart car system inside this Jeep, controlling several systems remotely.
ABOVE: Miller in the Jeep in a separate hacking attempt in which the Jeep's breaks were remotely disabled. Photo by Andy Greenberg for Wired.

ABOVE: Charlie Miller and Chris Valasek hacking into the Jeep, photo by Whitney Curtis for Wired.
According to Miller, as of last night, the newest update to Uconnect fixes the exploit they've enacted.
All is well. For now.
The team plans on speaking about their exploit at Black Hat 2015, an event dedicated to software hacks, exploits, and most important of all SECURITY.
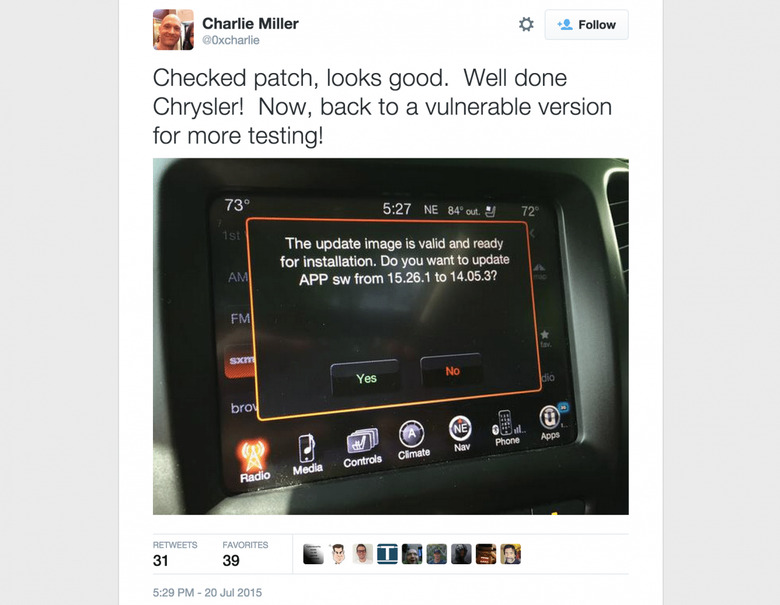
Working with the people behind the car's software systems, these researchers delivered word of their exploit well before letting it be known to the public. All is patched, all is well.
Miller says that "the patch for this issue was released last week." If you have a Chrysler, Ram, Durango, or Jeep, you really should bring it in to your local dealer and ask for all updates to be installed – unless you can do it yourself, in which case, go for it!
