Flashback Malware Grabbed Hackers $10k A Day
The folks responsible for the Apple-affected malware by the name of Flashback have had their activities analyzed today and it would appear that they're cashing in at $10,0000 a day. That's a lot of cash they're earning from an Apple hack that's spread across the web like a brush fire over the past few weeks. Apple has provided a fix for the malware already, but as there are quite a few people out there in the computing world that have no idea Flashback is affecting them right this second, the cash continues to flow. Where's that cash coming from, you might be asking?
As it appears, according to Symantec, the cash isn't $10k a day right now, but at the malware's peak – that very likely having been several weeks ago before the Apple fix. What we've got here is link redirection – when you click one link, you get an advertisement, or you get a pop-under advertisement window, or you simply get sent to a page you never intended to hit. It's a viciously simple situation, to be sure.
"The Flashback ad-clicking component is loaded into Chrome, Firefox, and Safari where it can intercept all GET and POST requests from the browser. Flashback specifically targets search queries made on Google and, depending on the search query, may redirect users to another page of the attacker's choosing, where they receive revenue from the click . (Google never receives the intended ad click.)" – Symantec
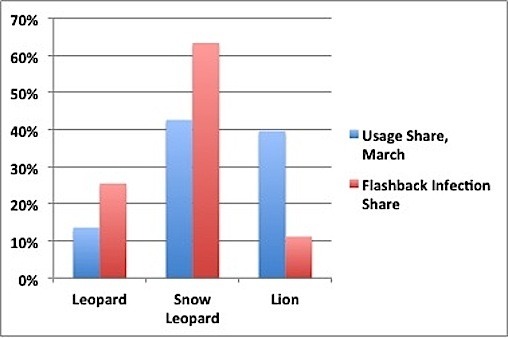
So what the makers of this malware are doing is collecting ad revenue from ads the user never wanted to click or see in the first place, the report showing 100,000 connections according to Symantec, this showing a breakdown across Leopard, Snow Leopard, and Lion. If you think there's any way at all you might be infected -even if you don't suspect and simply want to be safe, head back to the two step instructions to fix via Apple. It's simple!
[via MacRumors]
