EA Origin Exploit Leaves 40m At Potential Hack Risk
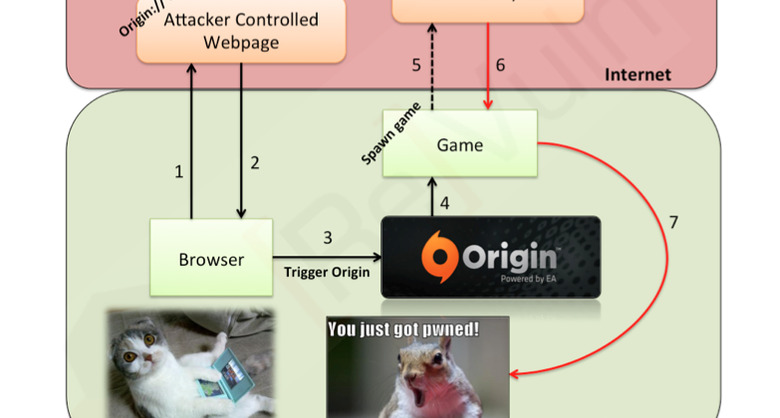
A vulnerability in EA's Origin online gaming platform could allow remote hackers to run dangerous code on gamers' computers without permission, by perverting links used to load titles like Crysis 3, its been revealed. Identified by ReVuln researchers Luigi Auriemma and Donato Ferrante, and presented last week at the Black Hat security conference, the exploit relies on the URI links the Origin desktop client uses to trigger local software from the cloud, and which can be modified to install malware instead.
At its root, the hack [pdf link] is broadly similar to an exploit explored last October by the same research team. The URI links can be tweaked to point to compromised Windows .dll files, which themselves can be used to download malware, tracking software, tools to extract personal details from the user's local files, or other spyware.
In the case of Crysis 3, the ReVuln researchers showed how a specially crafted link using Origin's "origin://LaunchGame/" URI terminology could even open up malware without the authors knowing what games were installed on the target PC. Should the user have allowed Origin to run all URI links without requiring specific approval each time, meanwhile, the exploit could be carried out completely transparently to them.
It's not an approach EA is unaware of, though it's uncertain whether the games company was aware of this specific hack. "Our team is constantly investigating hypotheticals like this one" a spokesperson told Ars Technica, "as we continually update our security infrastructure."
For the moment, the advice to the 40m gamers potentially at risk from exploits of this sort is to disable the "origin://" URI; that's possible with a tool like Nirsoft's URL Protocol View app. Games can still be run directly from Origin, but not using custom URIs.