AMD Ryzen May Have Major Security Flaws
AMD processors were the subject of a report on security vulnerabilities by CTSlabs this week. In the report, CTSlabs reported that some of the most secure portions of several different sorts of AMD processors were at risk of exploit by malicious parties. Those malicious parties would need to have access to the computer with the AMD processor, but once they've got that, they'd potentially be free to do one whole heck of a lot of damage.
To make the explanation of this situation as simple as possible, the folks at CTSlabs created a video. The video you see below explains the 13 "critical security vulnerabilities" these security researchers suggested they've found. They suggest that these flaws were found in both AMD Ryzen and EPYC product lines, and that these flaws are live, right now.
Four classes of vulnerabilities were discovered, according to CTSlabs. These four classes were dubbed Ryzenfall, Masterkey, Fallout, and Chimera. These names were selected due to their particular types – but man, they're generally cool-sounding enough to be the names of AMD gaming processors, aren't they? Imagine that.
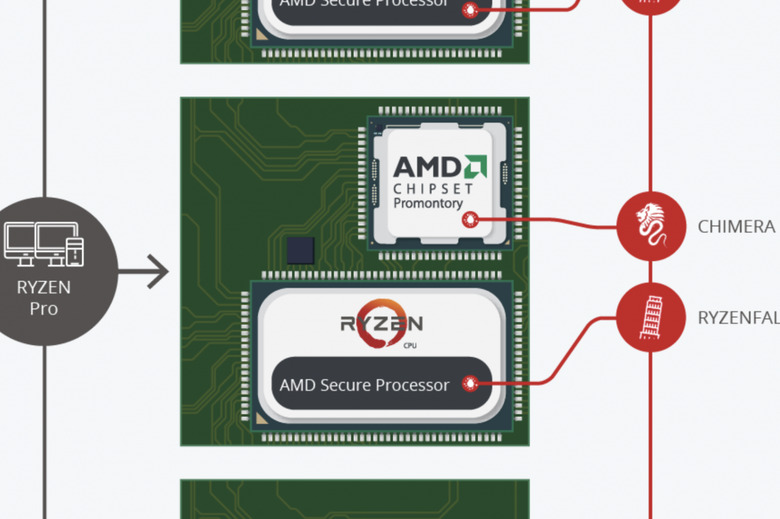
Ryzenfall allows the attacker to take control of an AMD Secure Processor on Ryzen Workstations, Ryzen Pro, and Ryzen Mobile. Fallout affects EPYC Servers, and allows attackers to read and write on SMRAM and memory (VTL-1) isolated by Windows Credential Guard.
Chimera affects Ryzen Workstations and Ryzen Pro and includes two sets of manufacturer backdoors. These backdoors, one in firmware, the other in hardware (ASIC), allow code injection into AMD Ryzen chipsets.
Masterkey was tested successfully on EPYC Servers and Ryzen Workstations and likely works on Ryzen Pro and Ryzen Mobile devices. With Masterkey, attackers are able to bypass Windows Credential Guard and tamper AMD firmware-based security, and infiltrate the Secure Processor through AMD's Secure Processor firmware. Masterkey is said to be capable of physical damage and/or otherwise bricking hardware.
CTSflaws made clear that Microsoft, AMD, and "a small number of companies that could produce patches and mitigations" were informed before the security group informed the press. All technical details that'd be of any use to potential hackers or malicious parties of any sort were redacted from the data posted by researchers.
As of publish time for this article, no solutions were listed or published by AMD or Microsoft, or related parties. Below is confirmation from Dan Guido of Trail of Bits that the security vulnerabilities are, indeed, real.
Regardless of the hype around the release, the bugs are real, accurately described in their technical report (which is not public afaik), and their exploit code works.
— Dan Guido (@dguido) March 13, 2018
If you or your business is potentially affected by this situation, hang tight. We're keeping our eyes open for solutions and workarounds and will post updates when they're released!