12 Ways Your Smartphone Might Be Tracking You
We're so attached to our smartphones that they've become like another limb, and the boundary between our physical and digital lives has increasingly blurred. You might even be reading this from a mobile device as we speak. This reliance raises many privacy concerns, as it exposes us to marketers and malicious actors eager to exploit our personal data.
Our smartphones act as double agents. In addition to the user experience, they are also used as surveillance tools, allowing outside parties to track our movements, purchases, and even conversations, leading to very suspicious targeted advertising that often feels invasive. It's become a running joke among friends and family — how just mentioning a product can seemingly summon ads for it out of thin air. What are the chances!?
Our smartphones hoover up and share sensitive data, often without clear consent. Our lives are simultaneously being tracked, and the importance of managing app permissions and understanding our smartphone tracking capabilities has never been more crucial. In this article we cover 12 ways your smartphone might be tracking you. While we connect and share with the world, let's remember to log out from vulnerabilities and set boundaries that keep our private lives just that — private.
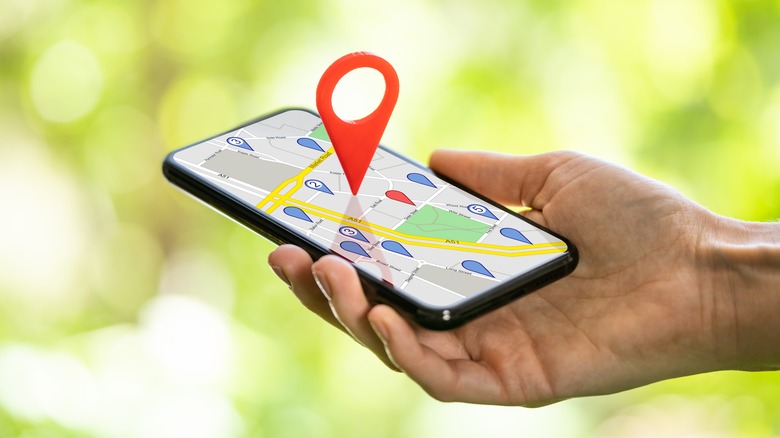
Location Tracking
Though it once seemed like something exclusive to spy movies, nowadays, smartphone tracking is frighteningly real. Indeed, our phones are tracking devices that record our movements with alarming precision through GPS, Wi-Fi, and cellular networks. GPS can directly track you via satellite, Wi-Fi can pinpoint locations based on network proximity, and cellular networks can triangulate your position through cell tower signals. This precision in location tracking has improved significantly, making it possible to trace your steps with near-exact accuracy. Like an eye in the sky.
Why does this matter? Well, there are many reasons why your phone tracking your location is a problem. For example, the information collected can be used for targeted advertising, improving service delivery — or more concerning, surveillance and data profiling. But wait, there's more! If you ever see a QR code at businesses or events, scanning one adds another way to track your movements by linking your physical location to online profiles or databases that can paint a picture of your habits and preferences.
Protecting yourself involves several steps. But one of the first actions you can take is to review and manage app permissions that request location access. Tap into your privacy settings on your smartphone to limit location sharing when you're not using an app. By being aware of these settings, you can put up your best defenses against unwarranted tracking and ensure that your movements remain as private as you want them to be.
Camera and Microphone Access
Another way your smartphone can monitor you is through the camera and microphone. Some apps use your phone's eyes and ears to listen in or watch you, sometimes even without consent. Face-scanning has become more prevalent, with social media apps letting users apply filters. And while you may look cute, what isn't is that some of these augmented reality features are gateways to gathering data about your immediate surroundings and habits and identifying you.
While some apps hide their intent, in China, you must have your facial data linked to your phone — it's even a requirement for getting a mobile plan. This helps to grow the country's existing database for facial recognition. It's a scary prospect having Big Brother watching your every move.
Elsewhere, voice assistants like Siri or Google Assistant can store sensitive information. And because these assistants are always keeping an ear out for the "Hey Google" or "Hey Siri" command, they're constantly listening. This level of eavesdropping can leave you feeling vulnerable, though there are ways for you to disable Google Assistant on Android and Siri on iPhone.
Email Tracking
Predating the internet itself, email remains the king of sending messages. However, this seemingly trusty method is still capable of tracking users. One particularly stealthy technique involves embedding a minuscule pixel, either as a .gif or .png. This 1x1-pixel is a camouflaged Trojan horse that is nearly invisible to the naked eye — hidden within the email's content, often matching the color of either the header, footer, or body.
This pixel can provide the sender info like if and when the email is opened, how often the email is opened, the kind of device used, and even the approximate location of the user based on their IP address. Sometimes, this data can pinpoint the user's location down to their street.
Other methods to track you are via the email service itself — some apps have faced criticism for harvesting data from users' inboxes and selling this information to third parties.
Ambient Light Sensor
Have you ever stepped indoors and noticed your smartphone's screen either dimmed or brightened? This magic is performed via your device's ambient light sensor, which is designed to enhance user experience by adjusting screen brightness to match your environment. Cool, huh?
Well, some companies got the bright idea that this functionality harbors another use beyond its intended capabilities — tapping into harvesting user data. Some apps and websites can use ambient light sensors to track users' browsing activities and even deduce specific interactions on the screen, like scrolling or swiping. This tracking method relies on detecting how user movements obstruct light patterns, and while they're subtle, they still offer a window into user behavior. Beyond simple tracking, it's possible to map out the interior of a building or a home based on light patterns captured by the smartphone. Feels like something out of a James Bond movie.
While this method of user tracking may not be widely known, it's important to understand that it's not foolproof and depends on factors like screen size and environment to be effective. Nevertheless, this intricate method highlights how smartphone sensors can be used for data collection, compromising privacy.
IMEI and IMSI Numbers
IMEI and IMSI numbers serve as unique identifiers for your smartphone and SIM card, respectively, and they're both used as precise tracking tools. Together, they can be used to track both the location and activity of your phone.
IMEI (International Mobile Equipment Identity) is a unique 15-digit number associated with your specific smartphone. Think of it as a pair of shoes you wear every day, and the soles have a unique pattern that leaves a distinct footprint wherever you go. Mobile phone operators and manufacturers use this number for identifying the device and for tracking purposes, whether to recover a lost phone or for law enforcement investigations.
IMSI (International Mobile Subscriber Identity) is a number linked directly to your mobile plan, whether a contract or a prepaid plan. You can think of this as a personal library card for mobile networks. It keeps track of your network usage, so if someone wants to know what you're "checking out," they could look at your IMSI number.
Cross-Device Tracking
As if our smartphones tracking us wasn't enough, we also need to consider cross-device tracking. This kind of tracking is a sophisticated technique that pesky advertisers and marketers use to keep tabs on consumer behavior across multiple devices using ultrasonic cross-device tracking (uXDT). This isn't the name of some exoplanet — this is happening right here on Earth, believe it or not. uXDT operates by emitting high-frequency sounds undetectable to the human ear. These signals serve as invisible bridges between our smartphones, tablets, and laptops.
Imagine you're sitting at home watching TV. Ultrasonic sounds are embedded in a commercial. Your phone or tablet is sitting on the table in another room and its microphone picks up the sound. Later, you purchase the product from the commercial on this same phone. This kind of detection gives advertisers a link to multiple devices to paint a more comprehensive picture of your behavior and preferences, like an invisible spiderweb.
uXDT is also embedded in radio commercials or hidden in JavaScript code in ads displayed in browsers, and there have been instances of mobile apps that actively listen for ultrasound without users' consent. This stealthy approach to tracking infringes on your privacy and blurs the line between the use of technology and personal space.
Health and Fitness Data
It comes as no surprise that health and fitness apps track us. We invite these apps to monitor a wide array of data points to gauge how we're making progress on our fitness journey. These apps track the number of steps we take, how far we jog, and even the flights of stairs we climb.
But beyond tracking our movements, these apps measure other things, such as heart rate, blood pressure, calories burnt, body temperature, and oxygen saturation levels. The more data provided, the better these apps are tailored to offer personal health and wellness plans. They can even track you in your sleep by analyzing sleep quality and patterns like duration and consistency.
All of this health and fitness data creates a digital blueprint of our physical being, data that is valuable to third parties such as advertisers and insurance companies, which can then sell it — sometimes without consent. Also, the security of this data isn't guaranteed, and data breaches can expose sensitive health information, leading to privacy violations and potential identity theft.
Social Media Monitoring
Every like, share, and comment you make on social media is tracked, painting a very detailed picture of your interests and behavior. As the saying goes, if the service is free, then you're the product. Social media platforms are a hotly debated topic, and how we use them determines what data is willingly shared not just with the public but also with third parties.
Collecting data from social media apps extends beyond what we share. These platforms use a sophisticated ecosystem of tracking mechanisms, like Apple's IDFA (Identifier for Advertisers) and Google's advertising ID. Our smartphones generate these identifiers, making cross-app and cross-site tracking easy. Detailed user profiles are created, and this information is shared with advertisers, data brokers, and other third parties that can then use the knowledge to tailor targeted ads or influence user behavior.
TikTok and other social media platforms have been scrutinized for their data-tracking practices. The app knows the videos you like and how much time you spend there. This info is used to refine content recommendations to capture more of your attention, like a person addicted to gambling with unlimited money to put in the never-ending dopamine slot machine. The extent of TikTok's data collection, concerns over its data privacy practices, and potential ties to foreign governments have sparked debates and investigations into how social media platforms track users.
Keyboard Input
Using a keyboard app seems like a good idea to upgrade your typing experience, but this convenience can come at a cost. While third-party keyboards may promise to record your keystrokes for "improvement purposes," this seemingly innocuous feature could be a gateway to a personal data breach. Every word you type, from usernames and passwords to credit card info and personal messages, could be logged and stored, potentially exposing you to identity theft, financial fraud, or unauthorized access to your online accounts. And it's not just keystrokes that pose a threat — the intrusion of keyloggers extends to the clipboard, a feature we often take for granted. This seemingly harmless copy-paste tool has been found to hoover up user data.
To stay on top of this, look for indicators of unauthorized keyboard monitoring, including quick battery drain, spikes in data usage, or weird app behavior. These warning signs could mean you have a background app that is monitoring or transmitting your keystrokes.
Network and Proximity-Based Tracking
It's a challenge to stay off the radar these days. It's not just our smartphones that are being used to track us, but a vast network of proximity-based tracking technologies in the physical world, which are more pervasive than we might realize.
If you've ever worked at the airport or in a public coffee shop, you most likely connected to an open Wi-Fi network. The network logs your approximate location, connection duration, and frequency of visits via your IP and MAC addresses, which act as unique identifiers on the internet and local networks. Your location and movements can be tracked across different Wi-Fi networks, and if you're using Bluetooth, when you pair smart devices or wearables you add to a digital map of your interactions and movements.
If you're out and about and decide to pop into a store, proximity-based tracking beacons may also be present. These beacons emit signals that interact with smartphones within their range. They can track your movements and even allow businesses to push notifications or ads straight to your phone.
Payment Information
It feels nice not to carry around a wallet, especially if you can just use your smartphone to pay. With Google Pay and Apple Wallet, you can tap or scan to make a purchase and be on your way. But each tap, scan, or transfer is logged, creating a complete picture of your spending habits. This data could be valuable to tech giants like Google, Apple, PayPal, and other merchants that might want to influence buyer behavior by pushing targeted ads based on past purchases.
So, everything from your favorite coffee shop to your monthly utility payments is turned into an open book for companies to analyze. As mobile payment apps become integral to everyday transactions, understanding the privacy implications of their use is important. Smartphone users need to weigh the benefits of convenience while protecting personal information from being exploited for targeted advertising.
Photo Metadata
Taking a picture using your smartphone is another way to be tracked. While taking a selfie or capturing a sunset may seem innocent enough, your phone is capturing more than what the eye can see. Each image includes metadata — details about the location, date, and time the photo was taken. This is part of the EXIF (Exchangeable Image File Format) data, which acts like a digital footprint. This embedded info can have unintended consequences, especially if you want to share it online.
One cautionary tale is the case of the late John McAfee, the eccentric tech millionaire who was on the run, evading Belizean authorities. McAfee's whereabouts were unknown until reporters from Vice magazine published a photo of him online. Unaware to them, the photo's metadata contained GPS coordinates that revealed McAfee was in Guatemala, leading to his arrest. It is ironic, given McAfee was making an unhackable phone, too.
It's worth noting that many social media platforms automatically strip EXIF data from photos when they are uploaded to protect users' privacy. Even so, it's important to be mindful of the information we may inadvertently share when posting images online and understand how to access photo metadata.